ssh.sshslowdns.com – In the realm of cybersecurity, WireGuard has emerged as a game-changer, offering unparalleled speed, security, and flexibility. And now, with WireGuard split tunneling, iOS users can enjoy the best of both worlds: enhanced privacy without compromising connectivity. In this comprehensive guide, we’ll delve into the world of WireGuard split tunneling on iOS, empowering you to configure, manage, and optimize your VPN connections like never before.
WireGuard split tunneling allows you to selectively route specific traffic through a VPN connection while leaving other traffic untouched. This means you can securely access private networks while maintaining local access to apps and services that require a direct connection.
Whether you’re a security-conscious individual or a professional seeking enhanced privacy, WireGuard split tunneling on iOS is an essential tool.
Overview of WireGuard Split Tunneling on iOS
WireGuard is an open-source VPN protocol known for its speed, security, and ease of use. Split tunneling is a feature that allows you to selectively route certain traffic through the VPN tunnel while other traffic goes through your regular internet connection.Split
tunneling on iOS devices offers several benefits, including:
- Enhanced privacy and security for sensitive traffic (e.g., banking, healthcare)
- Improved performance for local network resources (e.g., printers, file servers)
- Customization of VPN usage based on specific applications or websites
Use Cases for Split Tunneling on iOS
Some common use cases for split tunneling on iOS include:
- Accessing work resources while maintaining access to local devices
- Streaming geo-restricted content while using local banking apps
- Protecting sensitive data while browsing public Wi-Fi networks
- Bypassing VPN restrictions on certain websites or applications
Configuring WireGuard Split Tunneling on iOS
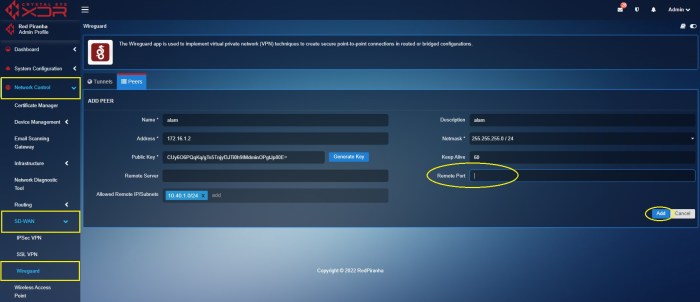
Configuring WireGuard split tunneling on iOS devices involves a few simple steps:
Importing the WireGuard Configuration
1. Open the WireGuard app on your iOS device.
2. Tap the “+” icon in the top right corner.
3. Select “Import from File” and navigate to the WireGuard configuration file (.conf) you want to import.
4. Enter a name for the connection and tap “Add.”
Enabling Split Tunneling
1. Tap on the connection you just imported.
2. Toggle the “Split Tunneling” switch to the “On” position.
3. Configure the “Allowed Apps” list by tapping on the “Add Apps” button and selecting the apps you want to exclude from the VPN tunnel.
Connecting to the VPN
1. Tap the “Connect” button in the top right corner of the connection screen.
2. Enter your WireGuard private key when prompted.
3. The connection will establish, and you will see a green “Connected” status in the app.
Managing WireGuard Split Tunneling Connections
Establishing and managing WireGuard split tunneling connections on iOS is straightforward. Once you have configured your profiles and connections, you can easily connect and disconnect from the VPN, as well as manage multiple connections and profiles.
Connecting and Disconnecting
To connect to a WireGuard split tunneling session, simply tap on the profile you want to use and then tap the “Connect” button. The connection will be established and you will be able to access the internet through the VPN.
To disconnect, tap on the “Disconnect” button.
Managing Multiple Connections and Profiles
You can have multiple WireGuard profiles configured on your iOS device, each with its own settings. This allows you to connect to different VPN servers or use different configurations for different purposes. To manage your profiles, tap on the “Profiles” tab in the WireGuard app.
Here you can add, delete, and edit profiles.You can also have multiple WireGuard connections active at the same time. This can be useful if you want to connect to different VPN servers simultaneously. To create a new connection, tap on the “+” button in the “Connections” tab and select the profile you want to use.
Troubleshooting WireGuard Split Tunneling Issues
WireGuard split tunneling on iOS is a powerful feature, but it can sometimes encounter issues. Here are some common problems and their solutions:
Connection Problems
- No internet access: Ensure that the WireGuard tunnel is active and that your device has an active internet connection.
- DNS issues: Check if your DNS settings are correct in the WireGuard configuration.
- Firewall blocking: Disable any firewalls that may be blocking the WireGuard connection.
Split Tunneling Problems
- Not all traffic is routed through the tunnel: Check the WireGuard configuration to ensure that the correct apps or domains are included in the allowed list.
- Split tunneling not working on specific apps: Update the affected apps and ensure that they are compatible with split tunneling.
Other Issues
- Configuration errors: Double-check the WireGuard configuration for any errors.
- Outdated software: Ensure that your iOS device and WireGuard app are up to date.
- Hardware issues: Try restarting your device or contacting Apple Support if you suspect hardware problems.
Security Considerations for WireGuard Split Tunneling
WireGuard split tunneling introduces certain security implications that must be carefully considered. Split tunneling allows specific traffic to bypass the VPN connection, potentially exposing sensitive data to external threats.
Best Practices for Securing WireGuard Connections
To mitigate these risks, it is essential to implement best practices for securing WireGuard connections:
- Use strong encryption: WireGuard employs robust encryption algorithms to protect data in transit. Ensure you use the latest encryption standards and key lengths.
- Implement authentication: Use strong authentication mechanisms such as public key infrastructure (PKI) to verify the identity of clients and servers.
- Monitor and log connections: Regularly monitor WireGuard connections for suspicious activity and maintain detailed logs for forensic analysis.
- Limit access: Restrict access to the WireGuard server and client configurations to authorized personnel only.
- Educate users: Train users on the importance of VPN security and the risks associated with split tunneling.
Comparison of WireGuard Split Tunneling to Other VPN Protocols
WireGuard split tunneling is a relatively new technology, and as such, there are not many other VPN protocols that offer the same level of functionality. However, there are a few other protocols that can be used to achieve similar results, such as OpenVPN and IPsec.OpenVPN
is a well-established VPN protocol that is known for its security and reliability. It is also relatively easy to configure and use. However, OpenVPN is not as fast as WireGuard, and it can be more resource-intensive.IPsec is another popular VPN protocol that is used by many businesses and organizations.
IPsec is very secure, but it can be complex to configure and manage. IPsec is also not as fast as WireGuard.Advantages of WireGuard Split Tunneling*
-*Speed
WireGuard is one of the fastest VPN protocols available. This makes it a good choice for applications that require high bandwidth, such as streaming video or gaming.
-
- -*Security
WireGuard is a very secure VPN protocol. It uses modern cryptography algorithms to protect your data from eavesdropping and tampering.
- -*Security
-*Ease of use
WireGuard is relatively easy to configure and use. This makes it a good choice for users who are not familiar with VPNs.
Disadvantages of WireGuard Split Tunneling*
-*New technology
WireGuard is a relatively new technology, and as such, it is not as well-supported as some other VPN protocols.
-*Limited features
WireGuard does not offer as many features as some other VPN protocols, such as support for multiple protocols or the ability to use different encryption algorithms.
ConclusionWireGuard split tunneling is a new technology that offers a number of advantages over other VPN protocols. It is fast, secure, and easy to use. However, it is important to note that WireGuard is still a relatively new technology, and it does not offer as many features as some other VPN protocols.
Advanced Configuration Options for WireGuard Split Tunneling
WireGuard split tunneling on iOS offers several advanced configuration options that allow for fine-tuning the behavior of the VPN connection. These options provide greater flexibility and control over how traffic is routed through the VPN tunnel.
One of the most useful advanced configuration options is the ability to specify custom DNS servers. By default, WireGuard uses the DNS servers provided by the VPN provider. However, you can override these settings and specify your own preferred DNS servers.
This can be useful if you want to use a specific DNS service, such as a privacy-focused DNS provider.
AllowedIPs
The AllowedIPs option allows you to specify a list of IP addresses or subnets that are allowed to pass through the VPN tunnel. This can be useful if you want to only route specific traffic through the VPN, while allowing other traffic to bypass the tunnel.
For example, you could use this option to allow traffic to your local network to bypass the VPN, while routing all other traffic through the tunnel.
ExcludedIPs
The ExcludedIPs option is the opposite of the AllowedIPs option. It allows you to specify a list of IP addresses or subnets that are excluded from the VPN tunnel. This can be useful if you want to prevent specific traffic from being routed through the VPN.
For example, you could use this option to exclude traffic to your local network from the VPN tunnel.
PeerDNS
The PeerDNS option controls whether or not DNS requests are sent through the VPN tunnel. By default, DNS requests are sent through the VPN tunnel. However, you can disable this option if you want to use your local DNS server.
MTU
The MTU (Maximum Transmission Unit) option allows you to specify the maximum size of packets that can be sent through the VPN tunnel. The default MTU is 1500 bytes. However, you may need to increase the MTU if you are experiencing packet fragmentation.
Integrating WireGuard Split Tunneling with Other Apps
WireGuard split tunneling on iOS devices can be seamlessly integrated with other apps, enhancing privacy and security without compromising connectivity. This integration allows you to route specific traffic through the VPN tunnel while excluding other apps or services from the encryption.
Using WireGuard with Specific Apps
WireGuard split tunneling can be configured to work with specific apps on your iOS device. For instance, you can set up WireGuard to route all internet traffic from your web browser through the VPN tunnel, ensuring privacy while browsing sensitive websites.
Simultaneously, you can exclude apps like banking or messaging apps from the tunnel, allowing them to connect directly to the internet for optimal performance.By selectively routing traffic through the VPN tunnel, WireGuard split tunneling provides a flexible and customizable solution that balances privacy and connectivity needs.
Automating WireGuard Split Tunneling Connections
Automating the connection and disconnection of WireGuard split tunneling sessions enhances efficiency and reduces manual intervention. This section explores techniques for automating these processes.
Various methods can be employed for automation, including scripts, automation tools, and systemd services. Scripts provide a straightforward approach, allowing you to define specific actions to be executed automatically. Automation tools offer a more comprehensive solution, enabling the creation of complex workflows and the integration of multiple tasks.
Using Scripts
To automate WireGuard split tunneling connections using scripts, follow these steps:
-
- Create a script file with a suitable name, such as
wg-split-tunnel.sh. - Include the following commands in the script:
- Create a script file with a suitable name, such as
#!/bin/bash
# Connect to WireGuard split tunnel
wg-quick up wg0
# Disconnect from WireGuard split tunnel
wg-quick down wg0 -
- Make the script executable by running the following command:
chmod +x wg-split-tunnel.sh -
- To connect to the split tunnel, run the script with the following command:
./wg-split-tunnel.sh
connect
-
- To disconnect from the split tunnel, run the script with the following command:
./wg-split-tunnel.sh disconnect Using Automation Tools
Automation tools, such as Ansible or Puppet, provide a more advanced approach to automating WireGuard split tunneling connections.
These tools allow for the creation of playbooks or manifests that define the desired state of the system. By leveraging these tools, you can automate complex tasks, such as configuring the WireGuard interface, setting up firewall rules, and managing the connection status.
Best Practices for Using WireGuard Split Tunneling on iOS
WireGuard split tunneling on iOS offers enhanced security and privacy by selectively routing traffic through the VPN tunnel. To optimize its usage, consider the following best practices: