ssh.sshslowdns.com – SSH server Ubuntu stand as indispensable tools, enabling seamless and encrypted connections between devices across networks. In this comprehensive guide, we delve into the world of SSH servers on Ubuntu, exploring their purpose, functionality, and best practices for installation, configuration, and security.
SSH servers Ubuntu provide a secure channel for remote login, file transfer, and command execution, making them essential for system administrators, developers, and anyone requiring secure remote access. As we journey through this guide, we will empower you with the knowledge and skills to establish and manage a robust SSH server on your Ubuntu system.
SSH Server Overview
An SSH server Ubuntu, short for Secure Shell server, is a program that allows secure remote access to a computer system over an unsecured network. It provides a secure channel for communication between two computers, enabling users to execute commands, transfer files, and manage systems remotely.
SSH servers offer numerous benefits, including:
- Secure communication: SSH encrypts all data transmitted between the client and server, ensuring confidentiality and integrity.
- Remote access: SSH allows users to access and manage remote systems from anywhere with an internet connection.
- Authentication and authorization: SSH provides various authentication methods, including passwords, public-key cryptography, and two-factor authentication, to control access to the server.
- File transfer: SSH supports secure file transfer using the Secure Copy Protocol (SCP) or SFTP (SSH File Transfer Protocol).
History and Evolution of SSH Servers
The first version of SSH, known as SSH-1, was developed in 1995 by Tatu Ylönen. It was designed to replace the insecure Telnet protocol. In 2006, SSH-2 was released, introducing significant improvements in security, speed, and functionality.
Today, SSH servers are widely used in various applications, including:
- Remote system administration
- Secure file transfers
- Network security monitoring
- Cloud computing
- Internet of Things (IoT) device management
Ubuntu SSH Server Installation
Installing an SSH server Ubuntu is a straightforward process that can be accomplished using various methods. This guide will provide detailed instructions on how to install an SSH server using the apt package manager and compiling from source, explaining the configuration options and parameters involved in each method.
Using apt
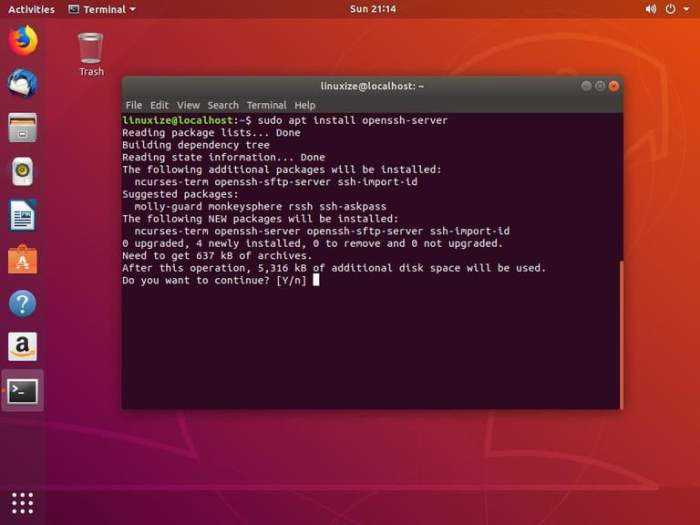
The apt package manager is the recommended method for installing software on Ubuntu. To install an SSH server using apt, run the following command:
sudo apt install openssh-server
This command will install the OpenSSH server package, which includes the SSH daemon (sshd) and related tools.
Compiling from source
While using apt is generally the preferred method for installing software on Ubuntu, it is also possible to compile SSH from source. This can be useful if you need to install a specific version of SSH or if you want to customize the build process.
To compile SSH from source, you will need to download the source code from the OpenSSH website. Once you have downloaded the source code, you can compile and install SSH by running the following commands:
./configure make sudo make install
These commands will compile and install SSH on your system. You may need to run the sudo ldconfig command to update the system’s dynamic linker cache.
Configuration
Once SSH is installed, you will need to configure it. The SSH configuration file is located at /etc/ssh/sshd_config . You can edit this file using a text editor such as nano or vim.
The SSH configuration file contains a number of options that you can configure. Some of the most common options include:
- Port: The port that SSH will listen on. The default port is 22.
- Protocol: The SSH protocol version that will be used. The default protocol is 2.
- Ciphers: The encryption ciphers that will be used. The default ciphers are AES-256-CBC, AES-192-CBC, and AES-128-CBC.
- MACs: The message authentication codes (MACs) that will be used. The default MACs are HMAC-SHA2-256, HMAC-SHA2-512, and HMAC-SHA1.
- Key exchange algorithms: The key exchange algorithms that will be used. The default key exchange algorithms are diffie-hellman-group-exchange-sha256, diffie-hellman-group-exchange-sha1, and ecdh-sha2-nistp256.
You can find more information about the SSH configuration file in the SSH documentation.
SSH Server Configuration

Configuring the SSH server involves modifying its settings to meet specific security and performance requirements. This includes setting the port number, authentication methods, and access control policies.
Key Configuration Files
- /etc/ssh/sshd_config: Main configuration file for the SSH server, containing global settings and directives.
- /etc/ssh/ssh_config: Client-side configuration file, specifying user-specific preferences and settings.
Port Number
The SSH server listens for incoming connections on a specific port, typically port 22. To change the port, edit the Port directive in /etc/ssh/sshd_config and restart the SSH service.
Authentication Methods
SSH supports multiple authentication methods, including password-based, public key, and two-factor authentication. To configure authentication methods, edit the AuthenticationMethods directive in /etc/ssh/sshd_config .
Access Control
Access control allows you to restrict access to the SSH server based on specific criteria, such as IP address, user group, or command. To configure access control, use the AllowUsers , DenyUsers , AllowGroups , and DenyGroups directives in /etc/ssh/sshd_config .
Advanced Configuration Options
- Compression: Enable compression to reduce network traffic, but may impact performance.
- Protocol Version: Specify the SSH protocol version to be used, typically version 2.
- Ciphers and Key Exchange Algorithms: Configure the encryption algorithms used for data protection.
SSH Server Security

Securing an SSH server is essential for protecting your network from unauthorized access and malicious attacks. Common vulnerabilities include:
- Weak passwords
- Unpatched software
- Default configurations
- Brute force attacks
- Unauthorized access
SSH Server Authentication
SSH servers support various authentication methods to ensure secure access to remote systems. These methods include password-based authentication, public key authentication, and two-factor authentication.
Password-based authentication is the simplest method, where users provide their username and password to connect to the server. However, it is less secure compared to other methods.
Public key authentication is a more secure method, where users generate a pair of cryptographic keys: a public key and a private key. The public key is stored on the server, while the private key is kept secret by the user.
When a user attempts to connect, the server compares the user’s public key with the stored key to verify their identity.
Two-factor authentication adds an extra layer of security by requiring users to provide two different forms of identification, such as a password and a one-time password (OTP) sent to their mobile device. This method is more resistant to unauthorized access.
When configuring SSH authentication mechanisms, it is important to consider the security requirements of the environment. Public key authentication and two-factor authentication are recommended for increased security, while password-based authentication can be used for less critical systems or for temporary access.
SSH Server Access Control
Access control in SSH servers enables administrators to define and enforce rules for user access to the server’s resources. It involves configuring user permissions, group memberships, and restricting access to specific files or directories.
User Permissions and Group Memberships
User permissions determine the actions that a specific user can perform on the server. Permissions are typically assigned to files and directories and can be set for the following categories:
- Owner: The user who created the file or directory.
- Group: The group to which the user belongs.
- Others: All other users on the system.
Permissions are typically represented using three-letter codes:
- r: Read permission
- w: Write permission
- x: Execute permission
For example, a file with permissions of “rw-r–r–” means that the owner can read and write to the file, the group members can read the file, and all other users can only read the file.
Restricting Access to Specific Files or Directories
To restrict access to specific files or directories, administrators can use the following techniques:
- Chmod: Change the permissions of a file or directory using the “chmod” command.
- Chown: Change the ownership of a file or directory using the “chown” command.
- Chgrp: Change the group ownership of a file or directory using the “chgrp” command.
By carefully configuring access control settings, administrators can ensure that only authorized users have access to the appropriate resources on the SSH server.
SSH Server Logging and Monitoring
Logging and monitoring are essential for maintaining the security of an SSH server. They provide a way to track activity, identify potential security threats, and troubleshoot issues.
There are a number of different ways to configure SSH server logging and monitoring tools. One common approach is to use the syslog facility. Syslog is a standard logging system that is available on most Unix-like operating systems, including Ubuntu.
To configure SSH server logging to use syslog, you will need to edit the /etc/ssh/sshd_config file. Find the line that says “SyslogFacility” and change the value to “AUTHPRIV”. This will cause SSH to log all authentication-related messages to the syslog facility.
You can also use a dedicated SSH server logging and monitoring tool, such as Fail2ban or Logwatch. These tools can provide more advanced features, such as real-time monitoring and automated threat detection.
It is important to regularly review your SSH server logs for any suspicious activity. This can help you to identify potential security threats and take steps to mitigate them.
Types of SSH Server Logs
There are a number of different types of SSH server logs, each of which contains different information. The most common types of logs include:
- Auth log: This log contains information about all authentication attempts, both successful and unsuccessful.
- Session log: This log contains information about all SSH sessions, including the start and end time, the source and destination IP addresses, and the commands that were executed.
- Error log: This log contains information about any errors that occur during the operation of the SSH server.
Analyzing SSH Server Logs
When analyzing SSH server logs, it is important to look for any suspicious activity. This can include:
- Failed login attempts: These may indicate that someone is trying to brute-force their way into your server.
- Unusual activity: This may indicate that your server has been compromised.
- Errors: These may indicate that there is a problem with your SSH server configuration or that your server is under attack.
If you find any suspicious activity in your SSH server logs, you should take steps to investigate and mitigate the threat. This may involve changing your SSH server configuration, blocking suspicious IP addresses, or contacting your hosting provider.
SSH Server Troubleshooting
Troubleshooting SSH server issues involves identifying the root cause and applying appropriate solutions. Common problems include:
Authentication failures
Incorrect credentials, disabled accounts, or network issues.
Connection failures
Firewall blocking, incorrect port settings, or server unavailability.
Slow performance
High load, network latency, or hardware limitations.
Security vulnerabilities
Outdated software, weak passwords, or misconfigurations.
Step-by-Step Troubleshooting
Verify SSH server Ubuntu status
Check if the service is running and listening on the correct port.
Examine authentication logs
Review /var/log/auth.log for authentication failures and error messages.
Check firewall rules
Ensure that SSH port (default: 22) is allowed in both inbound and outbound firewall rules.
Analyze server load
Use commands like “top” or “htop” to monitor system resources and identify performance bottlenecks.
Inspect SSH configuration
Review /etc/ssh/sshd_config to check for any misconfigurations or outdated settings.
Advanced Troubleshooting
Packet sniffing
Use tools like Wireshark to capture and analyze SSH traffic for errors or security breaches.
Kernel debugging
Enable kernel debugging and analyze system logs to identify low-level issues.
Use of SSH debugging tools
Utilize SSH debugging tools like “ssh
- vvv” or “ssh
- d” to generate detailed debugging output.
SSH Server Performance Optimization
SSH server performance can be impacted by various factors, including network latency, server load, and encryption algorithms. Optimizing SSH server settings can significantly improve performance and enhance the user experience.
Reducing Latency
Latency refers to the delay in data transmission between the SSH client and server. To reduce latency:
- Choose a server with low latency to the client’s location.
- Use a fast and reliable network connection.
- Configure the SSH server to use a faster encryption algorithm, such as AES-128-CBC.
Increasing Throughput
Throughput refers to the amount of data that can be transmitted per unit time. To increase throughput:
- Increase the server’s memory and CPU resources.
- Use a more efficient compression algorithm, such as Zlib.
- Configure the SSH server to use multiplexed channels.
SSH Server Use Cases
SSH server are widely used in various industries and applications for secure remote access and management.
Remote Administration
SSH server enable remote administration of servers, network devices, and other IT infrastructure components. System administrators can securely connect to remote systems from any location with an internet connection, perform maintenance tasks, troubleshoot issues, and manage configurations.
Secure File Transfer
SSH provides a secure channel for transferring files between systems. It uses strong encryption algorithms to protect data in transit, ensuring confidentiality and integrity. This makes SSH an ideal solution for transferring sensitive data, such as financial records, customer information, or intellectual property.
Application Access
SSH server Ubuntu can be used to securely access applications running on remote systems. This is particularly useful for accessing applications that are not accessible via the internet, such as internal databases, development environments, or custom software.
Remote Collaboration
SSH allows multiple users to connect to a remote system simultaneously and collaborate on tasks. This is beneficial for teams working on projects together, such as software development, system administration, or research.
Audit and Compliance
SSH server Ubuntu can be configured to log all access attempts and commands executed by users. This audit trail can be used to monitor user activity, detect security breaches, and comply with industry regulations and standards.