In the realm of network security, the ability to establish secure and reliable remote connections is paramount. SSH (Secure Shell) has emerged as a ubiquitous protocol for encrypted communication, while UDP (User Datagram Protocol) offers a lightweight and efficient transport layer.
By combining these technologies, we can create SSH tunnels over UDP, enabling secure data transfer and remote access even in challenging network environments.
In this comprehensive guide, we will delve into the intricacies of creating SSH tunnels over UDP. We will explore the fundamental concepts, step-by-step instructions, security considerations, troubleshooting techniques, and real-world applications of this powerful technique.
Understanding SSH and UDP

SSH (Secure Shell) is a network protocol that provides secure remote access to a computer system. It encrypts all traffic, including user authentication, commands, and data transfers, making it a popular choice for secure remote administration and file transfers.UDP (User Datagram Protocol) is a connectionless network protocol that operates at the transport layer.
Unlike TCP (Transmission Control Protocol), UDP does not establish a connection before sending data, making it more suitable for applications that require low latency and high throughput, such as online gaming and video streaming.While both SSH and UDP are network protocols, they serve different purposes and operate at different layers of the network stack.
SSH is a secure remote access protocol that operates at the application layer, while UDP is a connectionless transport protocol that operates at the transport layer.
Creating an SSH Tunnel over UDP
To create an SSH tunnel over UDP, follow these steps:
-
- Generate an SSH key pair using the command:
ssh-keygen -t rsa -b 4096
-
- Copy the public key to the remote server using:
ssh-copy-id user@remote_server
-
- On the client side, establish a UDP tunnel to the remote server using:
ssh -f -N -L 127.0.0.1:5000:localhost:22 -p 2222 user@remote_server
- Replace ‘user’ with your username, ‘remote_server’ with the remote server’s address, ‘2222’ with the port number for the SSH tunnel, ‘127.0.0.1’ with the local IP address, and ‘5000’ with the local port number.
Benefits of using UDP for SSH tunneling:
- Lower latency and faster speeds compared to TCP.
- Reduced overhead and improved performance for applications that don’t require reliable data delivery.
Limitations of using UDP for SSH tunneling:
- UDP is a connectionless protocol, so packets can be lost or reordered.
- Not suitable for applications that require reliable data delivery, such as file transfers or remote desktop sessions.
Securing SSH over UDP
SSH over UDP offers flexibility and performance advantages, but it also presents unique security considerations. Encrypting and authenticating SSH traffic over UDP is crucial to mitigate potential vulnerabilities.
Encryption Methods
SSH over UDP supports various encryption algorithms, including AES, 3DES, and Blowfish. These algorithms ensure the confidentiality of SSH traffic, preventing eavesdropping and data interception.
Authentication Mechanisms
SSH over UDP supports public-key authentication, which is considered more secure than password-based authentication. Public-key authentication relies on cryptographic key pairs to verify the identity of the client and server.
Best Practices for Securing SSH Tunnels
*
-*Use strong encryption algorithms
Opt for robust encryption algorithms like AES-256 or ChaCha20 to protect SSH traffic from decryption.
-
- -*Implement public-key authentication Public-key authentication provides a higher level of security compared to password-based authentication.
-*Restrict access to SSH tunnels
Limit access to SSH tunnels only to authorized users and devices.
-*Monitor and audit SSH activity
Regularly monitor SSH logs and audit SSH connections to detect suspicious activity.
-*Keep software up to date
Ensure that SSH servers and clients are updated with the latest security patches and fixes.
Troubleshooting SSH over UDP
SSH over UDP can occasionally encounter issues that require troubleshooting. Common problems and their solutions are listed below:
Identifying Common Problems
Common issues include:
- Connection failures
- Slow or unstable connections
- Security concerns
Troubleshooting Tips and Solutions
To resolve these issues, try the following:
- Connection failures: Check firewall settings, network connectivity, and UDP port configuration.
- Slow or unstable connections: Optimize network settings, adjust UDP buffer sizes, and consider using a VPN.
- Security concerns: Use strong encryption, disable unnecessary services, and monitor SSH logs for suspicious activity.
Advanced Troubleshooting Techniques
For more complex issues, consider:
- Using packet sniffers to analyze network traffic
- Enabling SSH debug mode to gather diagnostic information
- Consulting SSH documentation and online forums for additional support
Applications of SSH over UDP
SSH over UDP finds its applications in various real-world scenarios. Let’s explore a few key use cases:
Remote Access
SSH over UDP is often used for remote access to servers or devices located in different networks or geographical locations. It provides a secure and reliable way to connect to remote systems, execute commands, transfer files, and manage system configurations.
Network Security
SSH over UDP can be used to create secure tunnels for transmitting sensitive data over insecure networks. By encapsulating data within SSH packets, organizations can protect their communications from eavesdropping, data manipulation, and other security threats.
Other Applications
Beyond remote access and network security, SSH over UDP has been successfully deployed in various industries for specific purposes:
- In the financial sector, SSH over UDP is used for secure remote access to trading platforms and other critical systems.
- In healthcare, SSH over UDP enables secure communication between medical devices and remote monitoring systems.
- In the military, SSH over UDP is used for secure data transmission and communication in tactical environments.
Performance Optimization for SSH over UDP
SSH over UDP offers several advantages over SSH over TCP, including reduced latency and improved performance for certain types of applications. However, there are also some factors that can affect the performance of SSH over UDP, such as network congestion, packet loss, and firewall configurations.
Factors Affecting Performance
The following factors can affect the performance of SSH over UDP:
- Network congestion: Congestion on the network can cause packets to be delayed or dropped, which can impact the performance of SSH over UDP.
- Packet loss: Packet loss can occur due to a variety of factors, such as network congestion, hardware errors, or software bugs. Packet loss can also impact the performance of SSH over UDP.
- Firewall configurations: Firewalls can block or delay packets, which can impact the performance of SSH over UDP. It is important to configure firewalls to allow SSH over UDP traffic.
Tips for Optimizing Performance
There are a number of tips and techniques that can be used to optimize the performance of SSH over UDP:
- Use a reliable network connection: A reliable network connection is essential for good SSH over UDP performance. If the network connection is unreliable, packets may be delayed or dropped, which can impact the performance of SSH over UDP.
- Minimize packet loss: Packet loss can be minimized by using a reliable network connection and by using error correction techniques. Error correction techniques can help to recover lost packets, which can improve the performance of SSH over UDP.
- Configure firewalls correctly: Firewalls should be configured to allow SSH over UDP traffic. If firewalls are not configured correctly, packets may be blocked or delayed, which can impact the performance of SSH over UDP.
- Use a high-performance SSH server: A high-performance SSH server can help to improve the performance of SSH over UDP. High-performance SSH servers are designed to handle a large number of connections and to process packets quickly.
Trade-offs between Performance and Security
There are some trade-offs between performance and security when using SSH over UDP. For example, using a high-performance SSH server can improve the performance of SSH over UDP, but it may also increase the risk of security vulnerabilities. It is important to weigh the performance and security benefits of SSH over UDP carefully when making decisions about how to configure and use SSH over UDP.
Alternative Protocols for SSH over UDP
While SSH over UDP is a robust and widely used protocol, there are alternative protocols that offer different features and benefits. These protocols may be more suitable for specific use cases or environments.
One alternative protocol is Stunnel, which is a general-purpose SSL/TLS tunneling application. Stunnel can be used to create a secure tunnel between two hosts, and it supports a variety of protocols, including SSH. Stunnel is often used to secure web traffic, but it can also be used to create SSH tunnels over UDP.
Another alternative protocol is OpenSSH with the -u option. This option allows OpenSSH to create SSH tunnels over UDP. OpenSSH with the -u option is not as widely supported as Stunnel, but it is a more lightweight and efficient option.
Comparison of Alternative Protocols
| Protocol | Features | Advantages | Disadvantages ||—|—|—|—|| Stunnel | General-purpose SSL/TLS tunneling | Supports a variety of protocols | More complex to configure || OpenSSH with
u | Lightweight and efficient | Not as widely supported |
| SSH over UDP | Built-in support in OpenSSH | Widely supported | Can be less efficient than Stunnel |
Advantages and Disadvantages of Alternative Protocols
Advantages:*
-*Increased flexibility
Alternative protocols provide more flexibility in terms of the protocols that can be tunneled and the environments in which they can be used.
-
- -*Improved performance Some alternative protocols can offer better performance than SSH over UDP, especially in high-latency environments.
-*Additional features
Some alternative protocols offer additional features, such as support for multiplexing and compression.
Disadvantages:*
-*Less widely supported
Alternative protocols may not be as widely supported as SSH over UDP, which can make it difficult to find compatible clients and servers.
-
- -*More complex configuration Some alternative protocols can be more complex to configure than SSH over UDP.
-*Security concerns
Some alternative protocols may have security vulnerabilities that are not present in SSH over UDP.
SSH over UDP in Cloud Environments
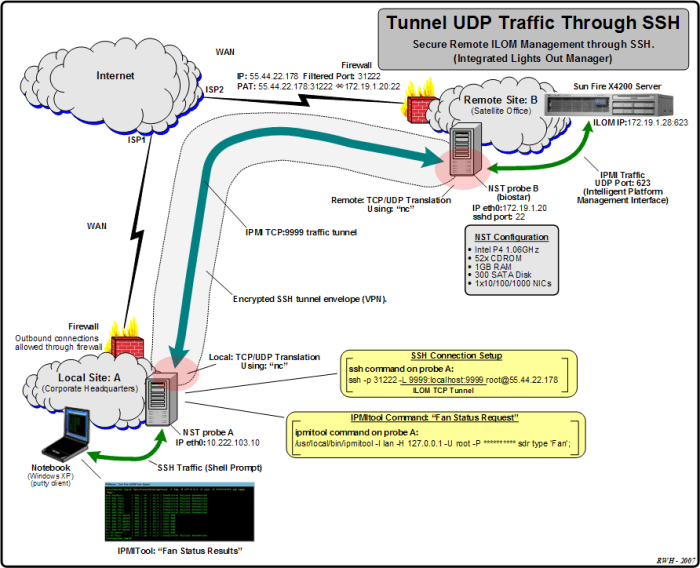
SSH over UDP offers several advantages in cloud environments, including reduced latency and improved performance, especially for applications that require real-time data transfer or low latency.
However, it also presents challenges, such as increased vulnerability to certain types of attacks and potential compatibility issues with some cloud platforms.
Best Practices for SSH over UDP in the Cloud
To successfully implement and manage SSH over UDP in the cloud, consider the following best practices:
-
- -*Configure firewalls Ensure that firewalls are configured to allow UDP traffic on the SSH port (typically port 22).
-*Use strong encryption
Employ strong encryption algorithms, such as AES-256, to protect data transmitted over the UDP tunnel.
-*Limit access
Restrict access to the SSH server by implementing authentication mechanisms such as SSH keys or multi-factor authentication.
-*Monitor and log
Regularly monitor SSH activity and logs to detect any suspicious or unauthorized access attempts.
-*Use a reputable cloud provider
Choose a cloud provider that supports SSH over UDP and provides robust security features to protect your data.
Emerging Trends in SSH over UDP
SSH over UDP has emerged as a compelling solution for secure remote access and tunneling, driven by the growing need for efficient and flexible network connectivity.
As technology advances, several notable trends are shaping the landscape of SSH over UDP:
One significant trend is the increasing adoption of SSH over UDP in cloud environments. Cloud computing platforms offer scalable and cost-effective solutions for businesses and organizations, and SSH over UDP provides a secure and efficient way to manage and access remote resources in the cloud.
Another emerging trend is the development of new applications and use cases for SSH over UDP. Beyond traditional remote access and tunneling, SSH over UDP is being explored for applications such as secure IoT device management, remote desktop sharing, and high-performance data transfer.
Additionally, the future of SSH over UDP is expected to be characterized by continued advancements in security and performance. New encryption algorithms and authentication mechanisms are being developed to enhance the security of SSH over UDP, while optimizations and enhancements are being made to improve its performance and scalability.
New Applications and Use Cases
SSH over UDP is finding new applications and use cases in various domains, including:
- Secure IoT Device Management: SSH over UDP provides a secure and efficient way to manage and configure IoT devices remotely, even in low-bandwidth and unreliable network conditions.
- Remote Desktop Sharing: SSH over UDP can be used for secure remote desktop sharing, enabling users to access their desktops from anywhere with a stable internet connection.
- High-Performance Data Transfer: SSH over UDP can be used for high-performance data transfer applications, such as file sharing and database replication, where speed and efficiency are critical.
Security and Performance Advancements
Ongoing advancements in security and performance are shaping the future of SSH over UDP:
- Enhanced Encryption Algorithms: New and more robust encryption algorithms, such as AES-256 and ChaCha20, are being adopted to enhance the security of SSH over UDP.
- Stronger Authentication Mechanisms: Stronger authentication mechanisms, such as two-factor authentication and public-key infrastructure (PKI), are being implemented to improve the security of SSH over UDP connections.
- Performance Optimizations: Optimizations and enhancements are being made to improve the performance and scalability of SSH over UDP, such as reducing latency and increasing throughput.
SSH over UDP for Advanced Users

SSH over UDP is a powerful tool that can be leveraged by advanced users to enhance their network security and performance. This section delves into advanced techniques, configurations, and use cases for SSH over UDP.
Maximizing Performance and Security
To maximize the performance and security of SSH over UDP, consider the following tips:
- Tune UDP buffer size: Adjust the UDP buffer size to optimize performance. A larger buffer can handle more data, but it can also increase latency.
- Use a firewall: Implement a firewall to restrict access to SSH over UDP ports and prevent unauthorized connections.
- Enable encryption: Use strong encryption algorithms to protect data transmitted over SSH over UDP.
- Disable unused protocols: Disable unnecessary SSH protocols, such as password authentication, to reduce the attack surface.
Advanced Use Cases
SSH over UDP has several advanced use cases, including:
- Network penetration testing: SSH over UDP can be used to bypass firewalls and access restricted networks.
- Forensic analysis: SSH over UDP can be used to collect evidence from compromised systems without alerting the attacker.
- Secure remote access: SSH over UDP can provide a secure and reliable way to access remote systems, even in environments with limited bandwidth or high latency.
Final Summary
Mastering the art of creating SSH tunnels over UDP empowers network administrators and security professionals with a versatile tool for secure remote access, network monitoring, and a myriad of other applications. By understanding the concepts, implementing best practices, and leveraging advanced techniques, you can harness the full potential of this technology to enhance the security and efficiency of your network infrastructure.