In the realm of virtual private networks (VPNs), WireGuard stands out as a revolutionary protocol renowned for its unparalleled speed, robust security, and user-friendly interface. When combined with Linux, WireGuard’s capabilities are further enhanced by the versatility of Linux systems, allowing for granular control over network traffic.
This comprehensive guide will delve into the intricacies of WireGuard Linux split tunneling, empowering you with the knowledge to configure and utilize this powerful technique. We will explore the concept of split tunneling, its benefits, and how WireGuard implements it.
We will also provide step-by-step instructions on configuring split tunneling in WireGuard, along with performance and security considerations.
WireGuard Overview
WireGuard is a cutting-edge VPN protocol designed to offer lightning-fast speeds, robust security, and a user-friendly experience. Unlike traditional VPN protocols, WireGuard utilizes a more modern and streamlined approach, resulting in exceptional performance and enhanced privacy protection.
One of the key advantages of WireGuard lies in its simplicity. It boasts a compact codebase, making it easier to maintain, audit, and implement. This streamlined design translates into significantly improved performance, allowing for faster connection speeds and lower latency.
Key Features of WireGuard
- Simplified Codebase: WireGuard’s compact codebase enhances its maintainability, auditability, and implementation.
- Cryptography: It employs state-of-the-art cryptography, including ChaCha20, Poly1305, Curve25519, and BLAKE2s, providing robust encryption and authentication.
- Speed: WireGuard’s optimized design results in exceptional connection speeds, minimizing latency and maximizing bandwidth utilization.
- User-Friendly: It features a user-friendly interface and straightforward configuration, making it accessible to both technical and non-technical users.
Linux Integration
WireGuard seamlessly integrates with Linux systems, offering enhanced security and flexibility for network connectivity.
Installing WireGuard on Linux
To install WireGuard on Linux, execute the following command in the terminal:“`sudo apt-get install wireguard“`
Configuration for Linux
After installation, configure WireGuard by creating a new interface file. For example, create a file named ‘wg0.conf’ in the ‘/etc/wireguard’ directory with the following content:“`[Interface]PrivateKey = Address = DNS =
[Peer] PublicKey = AllowedIPs = “`Once the configuration is complete, activate the interface:
“` sudo wg-quick up wg0 “`
Verify the connection using:
“` sudo wg show wg0 “`
Split Tunneling Concept
Split tunneling is a networking technique that allows specific traffic to bypass a VPN tunnel while other traffic is routed through it. This provides increased flexibility and control over network traffic, allowing users to access local resources and services without compromising the security of the VPN connection.
WireGuard implements split tunneling by allowing users to define rules that specify which traffic should be routed through the VPN tunnel and which traffic should be excluded. This allows users to customize their VPN configurations to meet their specific needs, such as accessing local network printers while still maintaining a secure connection to remote resources.
Benefits of Split Tunneling
Split tunneling offers several benefits, including:
- Improved performance: By excluding certain traffic from the VPN tunnel, split tunneling can reduce latency and improve overall network performance.
- Increased flexibility: Split tunneling allows users to tailor their VPN configurations to meet their specific needs, providing greater control over network traffic.
- Enhanced security: By isolating specific traffic from the VPN tunnel, split tunneling can help protect sensitive data from potential threats.
Configuring Split Tunneling
Configuring split tunneling in WireGuard involves specifying which traffic should be routed through the VPN tunnel and which should be sent directly to the internet. This is achieved by adding a “AllowedIPs” field to the peer configuration in the WireGuard configuration file.
To configure split tunneling, follow these steps:
1. In the WireGuard configuration file, add the “AllowedIPs” field to the peer configuration for the remote peer. 2. Specify the IP addresses or subnets that should be routed through the VPN tunnel. 3. Save the configuration file.
4. Restart the WireGuard service.
Example Configuration Files
Here is an example of a WireGuard configuration file with split tunneling enabled:
“` [Interface] PrivateKey = Address = 10.0.0.1/24 ListenPort = 51820
[Peer] PublicKey = AllowedIPs = 10.0.0.0/24, 192.168.0.0/24 “`In this example, all traffic to the 10.0.0.0/24 and 192.168.0.0/24 subnets will be routed through the VPN tunnel. All other traffic will be sent directly to the internet.
Performance Considerations
WireGuard’s performance implications with split tunneling are minimal compared to full tunneling. Split tunneling only encrypts specific traffic, reducing the overall computational overhead and bandwidth consumption.
Comparison to Other VPN Protocols
WireGuard outperforms traditional VPN protocols like OpenVPN and IPsec in terms of speed and latency. Its streamlined codebase and optimized kernel integration minimize overhead, resulting in faster connection speeds and lower latency.
- Speed: WireGuard’s lightweight design allows for higher data transfer rates, making it suitable for high-bandwidth applications like streaming and gaming.
- Latency: WireGuard’s low latency ensures a responsive connection, minimizing delays and interruptions in online activities like video conferencing and online gaming.
Overall, WireGuard with split tunneling offers a performance advantage over other VPN protocols while maintaining a high level of security and flexibility.
Security Implications
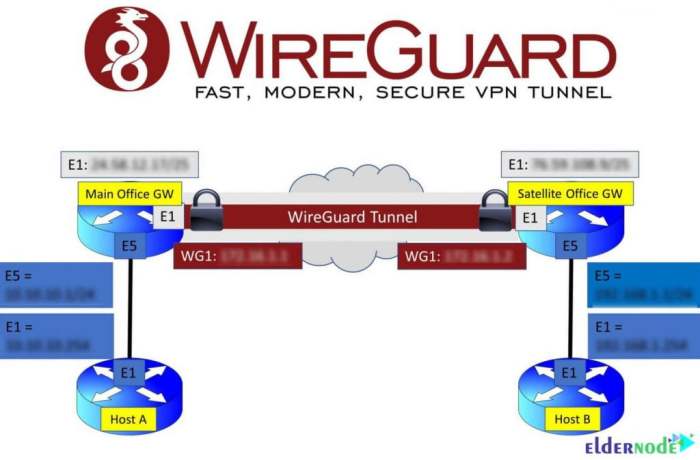
Split tunneling with WireGuard offers enhanced flexibility and efficiency, but it also introduces security considerations that must be carefully evaluated.
By selectively routing specific traffic through the VPN tunnel while allowing other traffic to bypass it, split tunneling can create potential vulnerabilities. It’s essential to understand these risks and implement appropriate mitigation strategies to ensure a robust security posture.
Risks of Split Tunneling
- Exposure to Untrusted Networks: Traffic outside the VPN tunnel remains unprotected, exposing devices and data to potential threats on untrusted networks, such as public Wi-Fi or malicious access points.
- DNS Leaks: If the VPN configuration is not properly configured, DNS requests may leak outside the tunnel, revealing the user’s online activities and potentially compromising privacy.
- IP Address Exposure: The IP address of the device is visible outside the VPN tunnel, making it possible for attackers to track the user’s online presence and location.
Mitigation Strategies
To mitigate these risks, several strategies can be employed:
- Careful Configuration: Ensure the VPN configuration is meticulously set up to prevent DNS leaks and IP address exposure. Use trusted DNS servers and configure the VPN client to block all traffic outside the tunnel.
- Network Segmentation: Implement network segmentation to isolate traffic from untrusted sources. Create separate subnets for devices that require VPN protection and those that can bypass the tunnel.
- Firewall Rules: Configure firewall rules to restrict access to the VPN subnet from untrusted networks. This prevents unauthorized access to the protected network.
- Strong Encryption: Use strong encryption protocols, such as AES-256, to protect data transmitted through the VPN tunnel.
- Regular Security Audits: Conduct regular security audits to identify potential vulnerabilities and ensure the split tunneling configuration remains secure.
Use Cases and Applications
WireGuard with split tunneling offers practical benefits in various industries and scenarios where selective routing of traffic is crucial.
One key application is in enterprise networks , where employees may need to access both internal resources and external websites simultaneously. Split tunneling allows them to securely connect to the corporate VPN while still accessing the internet directly, ensuring both privacy and seamless connectivity.
Government and Military
In the government and military sectors , secure communication is paramount. Split tunneling with WireGuard enables secure access to sensitive internal networks while allowing authorized personnel to access public websites or services as needed, enhancing both security and operational efficiency.
Healthcare
In the healthcare industry , where patient data privacy is critical, split tunneling with WireGuard provides a secure and compliant solution. Healthcare professionals can securely access patient records and other internal resources while still accessing the internet for research or communication purposes.
Troubleshooting and Support
Resolving common issues with WireGuard split tunneling requires a systematic approach. Start by checking the configuration files for errors, ensuring proper syntax and parameter values. Verify network connectivity, including the status of network interfaces and routing tables.
If issues persist, seek assistance from community forums and support channels. The WireGuard community is active on platforms like Reddit and GitHub, providing valuable insights and support from experienced users.
Community Forums
Community forums offer a wealth of information and support from the WireGuard community. Search for similar issues and solutions, or post your own questions for assistance.
- Reddit: r/wireguard
- GitHub: WireGuard GitHub Discussions
Support Channels
For more direct assistance, consider reaching out to support channels. WireGuard developers and maintainers may be available for assistance through:
- IRC: #wireguard on Libera.Chat
- Email: [email protected]
Advanced Configuration Options
WireGuard offers a range of advanced configuration options to customize split tunneling according to specific requirements. These options allow for fine-grained control over routing tables and firewall rules, enabling users to optimize network behavior and enhance security.
Customizing Routing Tables
By default, WireGuard creates a separate routing table for its traffic. However, users can modify this behavior by specifying custom routing rules. This allows for granular control over which traffic is routed through the VPN tunnel and which is sent over the regular internet connection.
For instance, a user may choose to route all traffic from a specific subnet or application through the VPN while allowing other traffic to bypass it.
Firewall Rules
WireGuard also provides the ability to configure firewall rules within the VPN interface. These rules determine which traffic is allowed to enter or exit the VPN tunnel. By customizing these rules, users can restrict access to specific ports or IP addresses, enhancing the security of their network.
For example, a user may block all incoming traffic except for essential services such as SSH or HTTPS.
Comparisons with Other VPN Solutions
WireGuard’s split tunneling capabilities offer unique advantages compared to other VPN solutions.
WireGuard’s lean codebase, high performance, and strong encryption make it a compelling choice for users seeking a secure and efficient VPN experience with granular control over network traffic.
OpenVPN
- Strengths: OpenVPN is an established and widely used VPN protocol, offering strong security and a range of customization options.
- Weaknesses: OpenVPN has a more complex configuration process and can be slower than WireGuard, especially on resource-constrained devices.
IPsec
- Strengths: IPsec is a versatile protocol that supports a wide range of encryption algorithms and can be integrated with existing network infrastructure.
- Weaknesses: IPsec can be complex to configure and manage, and its performance may not be as optimal as WireGuard’s.
IKEv2
- Strengths: IKEv2 is a modern VPN protocol that offers fast reconnection times and is suitable for mobile devices.
- Weaknesses: IKEv2 may not be as secure as WireGuard and can be more susceptible to certain types of attacks.
Summary
Mastering WireGuard Linux split tunneling unlocks a world of possibilities, enabling you to tailor your network connectivity to meet your specific requirements. Whether you seek enhanced privacy, improved performance, or granular control over your online activities, this guide will equip you with the knowledge and expertise to harness the full potential of WireGuard.