In the realm of secure network communications, the SSH UDP server stands out as a powerful tool. By leveraging the User Datagram Protocol (UDP), SSH UDP servers offer a unique combination of security and performance enhancements that cater to diverse use cases.
Unlike its TCP counterpart, SSH UDP operates on a connectionless model, providing faster data transfer and reduced latency. This makes it particularly suitable for applications where real-time communication and high throughput are crucial.
Overview of SSH UDP Server
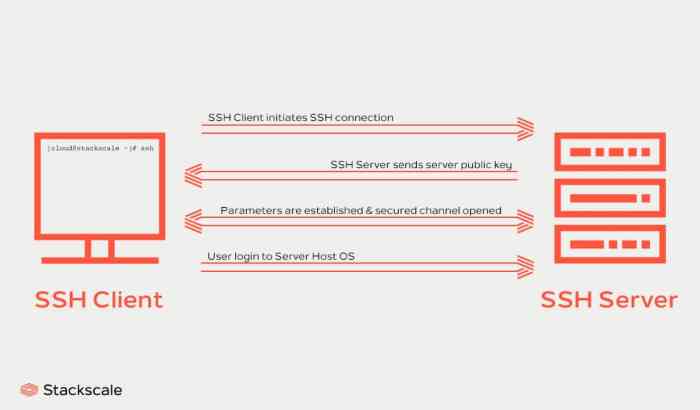
SSH UDP Server is a specialized implementation of the Secure Shell (SSH) protocol that operates over the User Datagram Protocol (UDP). Unlike the traditional SSH over TCP, which establishes a reliable connection, SSH over UDP utilizes a connectionless, datagram-based transport.This
unique approach offers both advantages and limitations. SSH UDP provides faster performance, particularly for applications that involve frequent short-lived connections or the transmission of small amounts of data. However, it comes with the drawback of lacking the reliability and error correction mechanisms inherent in TCP, making it less suitable for scenarios where data integrity and reliable delivery are critical.
Benefits of SSH UDP
- Improved performance: UDP’s connectionless nature eliminates the need for session establishment and teardown, resulting in faster response times and lower latency.
- Reduced overhead: UDP has a smaller header size compared to TCP, reducing the protocol overhead and maximizing data throughput.
- Suited for specific applications: SSH UDP is ideal for applications such as port forwarding, remote command execution, and network monitoring, where speed and efficiency are prioritized.
Limitations of SSH UDP
- Lack of reliability: UDP does not guarantee the delivery or sequencing of packets, which can lead to data loss or corruption.
- Limited error correction: UDP lacks built-in error correction mechanisms, making it susceptible to network errors and data integrity issues.
- Not suitable for large data transfers: SSH UDP is not recommended for transferring large files or streaming applications due to its unreliable nature.
In summary, SSH UDP Server offers advantages in performance and efficiency, making it suitable for specific applications where speed and low overhead are essential. However, its limitations in reliability and error correction should be carefully considered before deploying it in scenarios where data integrity and reliable delivery are paramount.
Configuration and Setup
Configuring an SSH UDP server involves establishing the server’s settings, including port forwarding, authentication methods, and security measures.
Port Forwarding
Configure the server to listen on a specific UDP port, typically port 22. This port will receive incoming SSH UDP traffic. Additionally, specify the target port to which the SSH UDP traffic will be forwarded.
Authentication Methods
Choose the authentication method for SSH UDP server access. Common options include:
Password-based authentication
Users provide a username and password to authenticate.
Public-key authentication
Users authenticate using a public-private key pair.
Security Settings
Implement security measures to protect the SSH UDP server, such as:
Firewalls
Restrict access to the SSH UDP server by allowing connections only from authorized IP addresses.
Rate limiting
Limit the number of authentication attempts per user to prevent brute-force attacks.
Disable unused services
Turn off any unnecessary services or protocols to reduce the attack surface.
Security Considerations
Running an SSH UDP server introduces unique security considerations that require careful attention.
The UDP protocol, unlike TCP, is connectionless and does not provide built-in mechanisms for authentication or data integrity. This inherent lack of security can lead to vulnerabilities and potential attacks.
Vulnerabilities and Best Practices
- Spoofing: UDP packets can be easily spoofed, allowing attackers to impersonate legitimate clients or servers.
- Eavesdropping: UDP traffic is not encrypted by default, making it susceptible to eavesdropping and interception of sensitive data.
- Amplification Attacks: UDP servers can be targeted by amplification attacks, where attackers exploit the lack of source address verification to amplify the impact of malicious traffic.
To mitigate these risks, it is crucial to implement robust security measures, including:
- Encryption: Encrypting UDP traffic using protocols like IPsec or SSH’s own encryption mechanisms ensures data confidentiality and integrity.
- Authentication: Employing strong authentication mechanisms, such as public-key cryptography or two-factor authentication, prevents unauthorized access to the server.
- Firewalls and ACLs: Implementing firewalls and access control lists (ACLs) can restrict access to the SSH UDP server only from trusted sources.
- Monitoring and Logging: Regularly monitoring server logs and employing intrusion detection systems can help detect and respond to potential attacks.
Performance Optimization
Optimizing the performance of an SSH UDP server is crucial for ensuring smooth and efficient remote access. Several factors can impact the performance, including network latency, packet size, and encryption algorithms. By understanding and addressing these factors, administrators can enhance the overall user experience.
Network Latency
Network latency refers to the delay in data transmission between the client and the server. High latency can significantly affect SSH performance, especially for interactive applications. To mitigate this issue, consider:
- Choosing a server physically close to the clients
- Using a fast and reliable network connection
- Reducing the number of network hops between the client and server
Packet Size
The size of UDP packets can impact performance. Smaller packets are processed faster, but they can lead to more overhead due to increased packet headers. Larger packets can reduce overhead, but they may experience fragmentation and reassembly delays. The optimal packet size depends on the network characteristics and application requirements.
Encryption Algorithms
The encryption algorithm used for SSH affects both security and performance. Stronger algorithms provide better protection, but they can be more computationally intensive. For performance-sensitive applications, consider using less computationally expensive algorithms while maintaining an acceptable level of security.
Use Cases and Applications
SSH UDP servers find practical applications in various scenarios. They offer secure remote access, reliable file transfers, and more.
SSH UDP servers provide a secure and efficient means of remote access to servers and devices. They enable system administrators and users to manage and control remote systems from any location with an internet connection.
Remote Access
- Remotely manage servers and devices from anywhere with internet access.
- Perform administrative tasks, such as software updates, configuration changes, and troubleshooting.
- Access graphical user interfaces (GUIs) of remote systems securely.
Secure File Transfer
- Transfer files securely between remote systems and local machines.
- Protect sensitive data during transfer using encryption and authentication.
- Automate file transfers using scripts or batch processes.
Other Applications
- Port forwarding: Redirect traffic from one port to another, allowing access to services that may be blocked by firewalls.
- SOCKS proxy: Enable secure access to remote networks through an SSH UDP server, bypassing firewalls and censorship.
- Network monitoring: Monitor network traffic and system performance remotely using SSH UDP servers.
Comparison with TCP
SSH UDP and SSH TCP are two different protocols used for secure remote access. SSH UDP is a newer protocol that offers several advantages over SSH TCP, including lower latency and increased bandwidth. However, SSH TCP is more widely supported and offers better security.In
general, SSH UDP is a better choice for applications that require low latency and high bandwidth, such as real-time audio and video streaming. SSH TCP is a better choice for applications that require high security, such as financial transactions or remote administration.
Advantages of SSH UDP
Lower latency
SSH UDP has lower latency than SSH TCP because it does not require a three-way handshake to establish a connection.
Increased bandwidth
SSH UDP can achieve higher bandwidth than SSH TCP because it uses a more efficient framing mechanism.
Reduced overhead
SSH UDP has less overhead than SSH TCP because it does not require the use of TCP headers.
Disadvantages of SSH UDP
Less widely supported
SSH UDP is not as widely supported as SSH TCP.
Less secure
SSH UDP is less secure than SSH TCP because it does not use a three-way handshake to establish a connection.
Advantages of SSH TCP
More widely supported
SSH TCP is more widely supported than SSH UDP.
More secure
SSH TCP is more secure than SSH UDP because it uses a three-way handshake to establish a connection.
Lower latency
SSH TCP has lower latency than SSH UDP in some cases, such as when the connection is over a long distance.
Disadvantages of SSH TCP
Higher latency
SSH TCP has higher latency than SSH UDP because it requires a three-way handshake to establish a connection.
Reduced bandwidth
SSH TCP can achieve lower bandwidth than SSH UDP because it uses a less efficient framing mechanism.
Increased overhead
SSH TCP has more overhead than SSH UDP because it requires the use of TCP headers.
Troubleshooting Common Issues
SSH UDP servers can encounter various problems during setup and operation. Understanding and resolving these issues is crucial for maintaining a stable and secure connection.
Common problems include:
- Connection failures due to incorrect port configuration or firewall restrictions.
- Data loss or corruption due to network congestion or UDP packet fragmentation.
- Security vulnerabilities such as unauthorized access or data interception.
To address these issues, consider the following solutions:
- Verify port configurations and firewall rules to ensure proper UDP traffic flow.
- Implement congestion control mechanisms and UDP packet fragmentation to prevent data loss.
- Enable encryption and authentication protocols to enhance security.
Advanced Features
SSH UDP servers offer advanced features that enhance security and flexibility.
These features include port knocking and dynamic port forwarding. Port knocking is a technique that allows authorized users to access a server by sending a sequence of packets to specific ports. This provides an additional layer of security by making it more difficult for unauthorized users to gain access to the server.
Dynamic Port Forwarding
Dynamic port forwarding allows users to create temporary connections between their local computer and a remote server. This is useful for accessing services that are not normally accessible from the internet, such as internal databases or file servers.
Examples and Case Studies
SSH UDP servers have proven their worth in various real-world scenarios, offering secure and efficient data transfer. Here are a few notable examples:
Secure Remote Access
A telecommunications company deployed an SSH UDP server to provide secure remote access to their network devices. This allowed their engineers to remotely manage and troubleshoot network issues from anywhere, ensuring uninterrupted service.
High-Performance Data Transfer
A large research institution used an SSH UDP server to transfer large scientific datasets between remote locations. The UDP protocol’s low overhead and high bandwidth capacity enabled fast and reliable data transmission, accelerating research progress.
Industrial Automation
An industrial automation company utilized an SSH UDP server to establish secure communication between programmable logic controllers (PLCs) in different manufacturing plants. This allowed them to monitor and control production processes remotely, improving efficiency and reducing downtime.
Future Trends and Developments

The realm of SSH UDP servers is on the cusp of exciting advancements that promise to reshape its capabilities and impact. Future developments in this domain are anticipated to focus on enhancing security, performance, and usability.
Enhanced Security
Security will remain a paramount concern, and SSH UDP servers are expected to incorporate advanced encryption algorithms and authentication protocols to safeguard data and protect against cyber threats. Multi-factor authentication, biometrics, and zero-trust principles are likely to gain prominence, bolstering the security posture of these servers.
Improved Performance
Performance optimization will be a key focus area, with innovations aimed at reducing latency, increasing bandwidth, and handling larger workloads. Adaptive congestion control algorithms, optimized packet handling, and the adoption of next-generation networking technologies will contribute to enhanced performance and scalability.
Simplified Usability
User experience will be a priority, with SSH UDP servers becoming more accessible and easier to manage. Automated configuration, intuitive interfaces, and simplified setup processes will make these servers more approachable for a wider range of users, reducing the technical expertise required for deployment and maintenance.
Emerging Applications
As SSH UDP servers evolve, they are expected to find applications in new and emerging areas. Cloud computing, edge computing, and the Internet of Things (IoT) are among the domains where SSH UDP servers are likely to play a significant role, enabling secure remote access, management, and data transfer.
Integration with AI
Artificial intelligence (AI) is poised to transform SSH UDP servers, enabling intelligent anomaly detection, automated threat mitigation, and proactive performance optimization. Machine learning algorithms will analyze server logs, network traffic, and user behavior to identify potential issues and take corrective actions autonomously.
Last Word
In conclusion, SSH UDP servers offer a compelling solution for secure and efficient network communication. Their unique advantages over TCP, coupled with advanced features and a wide range of applications, make them an indispensable tool for network administrators and security professionals alike.
As technology continues to evolve, SSH UDP servers are poised to play an even more prominent role in shaping the future of secure and high-performance network communications.