In the era of interconnected devices and remote work, the need for secure and efficient remote access to servers and systems has become paramount. SSH over WebSockets emerges as a groundbreaking technology that redefines remote connectivity, offering a seamless, secure, and real-time communication channel between clients and servers.
This article delves into the realm of SSH over WebSockets, exploring its concepts, benefits, applications, security considerations, performance optimization, and comparison with alternative remote access technologies. We will also shed light on popular open-source implementations, commercial solutions, future trends, and developments in this rapidly evolving field.
WebSockets Overview
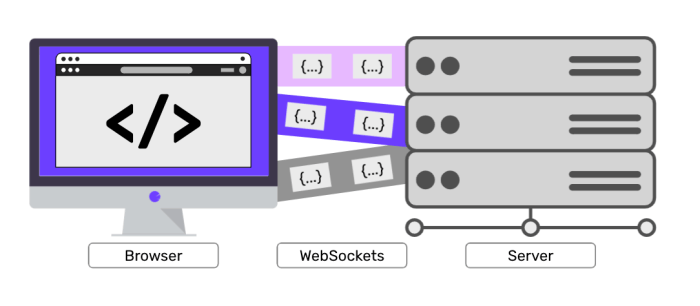
WebSockets are a revolutionary technology that enables real-time, bidirectional communication between web browsers and servers. Unlike traditional HTTP requests, which are short-lived and unidirectional, WebSockets establish a persistent connection that allows for continuous data exchange.
This breakthrough in web communication opens up a plethora of possibilities, particularly for applications that demand real-time updates, such as online gaming, chat applications, financial trading platforms, and collaborative editing tools.
Advantages of WebSockets
WebSockets offer several advantages over other technologies for real-time communication:
- Full-duplex communication: WebSockets enable simultaneous data transfer in both directions, facilitating real-time interactions.
- Low latency: The persistent connection established by WebSockets minimizes latency, ensuring near-instantaneous data exchange.
- Scalability: WebSockets can handle a large number of concurrent connections, making them suitable for applications with a high volume of users.
- Reduced server load: WebSockets reduce the load on the server by eliminating the need for constant polling or long-lived HTTP connections.
Disadvantages of WebSockets
Despite their advantages, WebSockets also have some drawbacks:
- Browser support: WebSockets require support from the web browser, which may not be available in all browsers or older versions.
- Security: WebSockets use the same port as HTTP (port 80) by default, which can pose security risks if not properly configured.
- Complexity: Implementing WebSockets requires more technical expertise compared to other technologies, such as long polling or server-sent events.
Applications of WebSockets
WebSockets have gained popularity in a wide range of applications, including:
- Online gaming: WebSockets enable real-time multiplayer gaming, allowing players to interact with each other in real time.
- Chat applications: WebSockets facilitate real-time messaging, enabling users to communicate instantaneously.
- Financial trading platforms: WebSockets provide real-time updates on stock prices, allowing traders to make informed decisions quickly.
- Collaborative editing tools: WebSockets allow multiple users to collaborate on documents or code in real time, enabling seamless collaboration.
SSH Over WebSockets
SSH over WebSockets is a technique that enables secure remote access to servers using the WebSocket protocol. It combines the features of SSH (Secure Shell) with the benefits of WebSockets, providing a modern and efficient way to establish secure connections over the web.
SSH over WebSockets offers several advantages over traditional SSH connections, including:
- Cross-platform Compatibility: WebSockets are supported by all major browsers and operating systems, making SSH over WebSockets accessible from a wide range of devices.
- Enhanced Security: WebSockets use the WebSocket Secure (WSS) protocol, which provides a secure and encrypted connection, protecting data from eavesdropping and tampering.
- Reduced Latency: WebSockets utilize a full-duplex communication channel, allowing for real-time data exchange with low latency, resulting in a more responsive and interactive user experience.
- Improved Performance: WebSockets enable efficient data transmission by leveraging binary frames, leading to improved performance, especially for applications that require frequent data updates.
Setting Up SSH Over WebSockets
To set up SSH over WebSockets, follow these steps:
- Install an SSH Server: Install an SSH server on the remote server you want to access. Popular options include OpenSSH, Dropbear, and Tectia.
- Enable SSH Over WebSockets: Configure your SSH server to support WebSockets. This typically involves editing the SSH configuration file (e.g., /etc/ssh/sshd_config) and enabling the “WebSocketsGateway” option.
- Install a WebSocket Client: Install a WebSocket client on the device you will use to access the remote server. Popular options include WebSocket++ and AutobahnJS.
- Connect to the SSH Server: Use the WebSocket client to connect to the SSH server using the WebSocket protocol. You will need to specify the server’s hostname or IP address, port number, and the SSH credentials.
- Interact with the Remote Server: Once connected, you can interact with the remote server as if you were using a traditional SSH connection. You can execute commands, transfer files, and manage the server’s resources.
Use Cases and Applications
SSH over WebSockets offers a versatile range of applications across various domains. Its ability to establish secure and real-time connections makes it particularly valuable in remote administration, DevOps, and cloud computing.
In remote administration, SSH over WebSockets enables IT professionals to securely access and manage remote servers, network devices, and virtual machines from any location with an internet connection. This allows administrators to perform tasks such as software installation, configuration changes, and troubleshooting, all through a web browser without the need for additional software or VPNs.
DevOps and Continuous Integration
In the DevOps and continuous integration (CI) world, SSH over WebSockets plays a crucial role in automating and streamlining development and deployment processes. It allows developers to seamlessly integrate SSH commands and scripts into their CI/CD pipelines, enabling automated testing, deployment, and configuration management.
This integration enhances the efficiency and reliability of the software development lifecycle.
Cloud Computing and Infrastructure Management
SSH over WebSockets finds its application in cloud computing and infrastructure management as well. Cloud providers and IT administrators can leverage this technology to securely access and manage cloud-based resources, virtual machines, and containers. This allows them to perform tasks such as OS updates, software installation, and configuration changes remotely, ensuring efficient management of cloud infrastructure.
Real-World Examples
- GitHub: GitHub, the popular code hosting platform, utilizes SSH over WebSockets to provide secure access to code repositories for developers. This allows developers to clone, push, and pull code changes directly from their web browser without the need for a separate SSH client.
- AWS: Amazon Web Services (AWS) offers a range of cloud-based services that can be managed using SSH over WebSockets. AWS Systems Manager, for instance, allows administrators to securely access and manage EC2 instances, containers, and other AWS resources through a web-based console.
- GitLab: GitLab, another popular code hosting platform, also incorporates SSH over WebSockets to facilitate secure access to code repositories and enable seamless integration with CI/CD pipelines.
Security Considerations
SSH over WebSockets presents unique security considerations due to the nature of WebSockets and the potential for vulnerabilities in SSH implementations. Understanding these risks and implementing appropriate security measures is crucial for maintaining the integrity and confidentiality of data transmitted over SSH over WebSockets connections.
Potential Vulnerabilities and Attacks
Several potential vulnerabilities and attacks can target SSH over WebSockets connections, including:
- Man-in-the-Middle (MITM) Attacks: Adversaries can intercept and manipulate data transmitted over SSH over WebSockets connections by posing as a legitimate server or client. This can lead to eavesdropping, data manipulation, or session hijacking.
- Cross-Site Request Forgery (CSRF) Attacks: Malicious websites or scripts can exploit vulnerabilities in web applications to send unauthorized SSH over WebSockets requests on behalf of legitimate users, potentially leading to unauthorized access or data exfiltration.
- WebSockets Hijacking: Attackers can exploit vulnerabilities in WebSockets implementations or underlying network infrastructure to hijack SSH over WebSockets connections, allowing them to impersonate legitimate users or inject malicious data into the communication channel.
- Buffer Overflow Attacks: Buffer overflow vulnerabilities in SSH implementations can be exploited to execute arbitrary code on the target system, potentially leading to remote code execution or privilege escalation.
- Denial-of-Service (DoS) Attacks: Attackers can launch DoS attacks against SSH over WebSockets servers by flooding them with excessive connection requests or sending malformed packets, disrupting legitimate user access.
Best Practices and Security Measures
To mitigate the risks associated with SSH over WebSockets, several best practices and security measures can be implemented:
- Use Strong Encryption: Employ robust encryption algorithms, such as AES-256 or ChaCha20, to protect data transmitted over SSH over WebSockets connections. This ensures that even if data is intercepted, it remains confidential.
- Implement Mutual Authentication: Utilize mutual authentication mechanisms, such as public-key cryptography or certificate-based authentication, to verify the identities of both the client and the server. This helps prevent unauthorized access and impersonation attacks.
- Enable Access Control: Implement access control mechanisms, such as role-based access control (RBAC) or attribute-based access control (ABAC), to restrict access to SSH over WebSockets connections based on user roles, attributes, or other relevant factors.
- Monitor and Log Activity: Continuously monitor SSH over WebSockets connections for suspicious activity, such as failed login attempts, unusual traffic patterns, or anomalous behavior. Implement logging mechanisms to record relevant events and facilitate incident investigation.
- Keep Software Up to Date: Regularly update SSH software and underlying operating systems to patch known vulnerabilities and address security issues. This helps prevent attackers from exploiting outdated software versions.
- Educate Users: Educate users about the security risks associated with SSH over WebSockets and provide guidance on secure practices, such as using strong passwords, being cautious of suspicious links or attachments, and reporting any suspicious activity.
Performance and Scalability
SSH over WebSockets exhibits varied performance characteristics depending on the specific scenario. Factors such as network conditions, server load, and client capabilities can significantly influence the overall performance and scalability of the connection.
Factors Impacting Performance
- Network Latency: High network latency can introduce noticeable delays in data transmission, affecting the responsiveness of SSH over WebSockets connections.
- Server Load: When the server is handling multiple SSH over WebSockets connections simultaneously, it can experience increased load, potentially leading to performance degradation.
- Client Capabilities: The capabilities of the client device, such as its processing power and network connectivity, can also impact the performance of SSH over WebSockets connections.
- Data Volume: The amount of data being transferred through the SSH over WebSockets connection can affect its performance. Larger data transfers may require more time and resources, potentially leading to slower speeds.
- WebSocket Implementation: The specific implementation of the WebSocket protocol on both the client and server sides can influence performance. Different implementations may exhibit varying levels of efficiency and scalability.
Optimizing Performance and Scalability
To optimize performance and scalability in SSH over WebSockets implementations, several recommendations can be considered:
- Minimize Network Latency: Reducing network latency is crucial for improving the responsiveness of SSH over WebSockets connections. This can be achieved by utilizing high-speed network connections, optimizing routing paths, and employing techniques like load balancing to distribute traffic across multiple servers.
- Manage Server Load: Proper load management is essential to prevent performance degradation due to excessive server load. This includes monitoring server resources, scaling the server infrastructure as needed, and implementing mechanisms to handle peak loads effectively.
- Utilize Efficient WebSocket Implementations: Selecting efficient and scalable WebSocket implementations for both the client and server sides is crucial for maximizing performance. Thorough research and testing can help identify the most suitable implementations for a specific use case.
- Optimize Data Transfer: Optimizing data transfer techniques can improve the performance of SSH over WebSockets connections. This includes compressing data to reduce its size, utilizing efficient data encoding schemes, and employing techniques like pipelining to minimize round-trip times.
- Monitor and Tune Performance: Regularly monitoring the performance of SSH over WebSockets connections is essential to identify potential bottlenecks and areas for improvement. Adjustments to configuration parameters, such as buffer sizes and connection timeouts, can be made to fine-tune performance.
Comparison with Alternatives
SSH over WebSockets offers a modern approach to remote access, complementing traditional methods like SSH, VPNs, and RDP. Each technology has its strengths and weaknesses, making it suitable for specific use cases. Understanding these differences helps organizations choose the best solution for their remote access needs.
Traditional SSH
Traditional SSH, a widely used remote access protocol, establishes a secure connection between a client and a server over a network. It allows users to securely log in to remote systems and execute commands, transfer files, and manage system resources.
SSH’s main advantage is its simplicity, reliability, and widespread support across platforms. However, it requires specific SSH clients and server configurations, which may be challenging for non-technical users.
VPNs
Virtual Private Networks (VPNs) create a secure private network over a public network, allowing users to access resources within the network remotely. VPNs offer comprehensive network-level security and can be used to access a wide range of resources, including file servers, applications, and websites.
However, VPNs can be complex to set up and manage, and they may introduce additional latency and performance overhead.
RDP
Remote Desktop Protocol (RDP) enables users to remotely control a computer over a network connection. RDP provides a graphical user interface (GUI) that allows users to interact with the remote computer as if they were physically present. RDP is commonly used for remote administration and support, as it offers fine-grained control over the remote system.
However, RDP is less secure than SSH and VPNs, and it may not be suitable for accessing sensitive data or systems.
Suitability for Different Use Cases
The choice of remote access technology depends on the specific use case and requirements. Here’s a brief overview of the suitability of each technology for different scenarios:
- Secure Shell Access: SSH over WebSockets and traditional SSH are ideal for securely accessing remote systems, executing commands, and managing files.
- Remote Administration and Support: RDP is commonly used for remote administration and support, as it provides a graphical interface for interacting with the remote system.
- Network-Level Security: VPNs are suitable for establishing secure network connections and accessing resources within a private network remotely.
- Web-Based Remote Access: SSH over WebSockets excels in web-based remote access, allowing users to securely connect to remote systems through a web browser.
Comparison Table
The following table summarizes the key differences and similarities between SSH over WebSockets and its alternatives:
| Technology | Protocol | Connection Type | Security | Ease of Use | Platform Support |
|---|---|---|---|---|---|
| SSH over WebSockets | WebSocket | Full-duplex, bidirectional | Encrypted | Moderate | Cross-platform |
| Traditional SSH | SSH | Full-duplex, bidirectional | Encrypted | Moderate | Cross-platform |
| VPNs | IPsec, OpenVPN, PPTP | Full-duplex, bidirectional | Encrypted | Complex | Cross-platform |
| RDP | RDP | Full-duplex, bidirectional | Less secure | Easy | Windows, macOS, Linux |
Open Source Implementations
SSH over WebSockets is supported by a range of open-source libraries and frameworks, offering various features and capabilities. These implementations empower developers to integrate SSH functionality into their web applications, enabling secure remote access and terminal sessions over a WebSocket connection.
To utilize these libraries, developers can follow specific installation and usage instructions provided by each project. Typically, these libraries offer comprehensive documentation and examples to guide developers through the integration process.
Popular Libraries and Frameworks
- SockJS: A JavaScript library that provides a WebSocket-like API, enabling fallback options for browsers that do not natively support WebSockets. SockJS supports SSH over WebSockets, allowing developers to establish secure connections and terminal sessions.
- Primus: A versatile JavaScript library that simplifies the implementation of real-time applications. Primus includes support for SSH over WebSockets, facilitating the creation of secure remote access solutions.
- xterm.js: A JavaScript library that renders a terminal emulator in the browser. It can be integrated with SSH over WebSockets libraries to provide a terminal-like interface for remote access and command execution.
- Secure Shell (SSH) Library for JavaScript (ssh.js): A comprehensive JavaScript library that offers a wide range of SSH features, including support for SSH over WebSockets. It enables developers to establish secure connections, transfer files, and execute commands remotely.
- WebSSH2: A Python library that facilitates SSH over WebSockets connections. It provides a simple and intuitive API for developers to integrate SSH functionality into their web applications.
Open-Source Projects Demonstrating SSH over WebSockets
- WebSSH: A popular open-source project that provides a web-based SSH client. It utilizes SockJS and xterm.js to establish SSH over WebSockets connections, enabling users to securely access remote servers and execute commands directly from their browser.
- SSH over WebSocket Proxy: A lightweight proxy server that enables SSH connections over a WebSocket tunnel. It allows users to securely access remote servers through a web browser, without the need for a dedicated SSH client.
- Terminal.js: A JavaScript library that provides a terminal emulator for the browser. It can be integrated with SSH over WebSockets libraries to create web-based terminal applications, allowing users to remotely access and manage servers.
Commercial Solutions
With the increasing demand for remote access and secure connectivity, several commercial solutions offer SSH over WebSockets functionality. These solutions provide a range of features, pricing options, and support services to cater to different business needs.
Features and Pricing Comparison
Commercial SSH over WebSockets solutions offer a variety of features, including:
- Secure and encrypted communication using SSH protocol over WebSockets.
- Cross-platform compatibility, allowing access from various devices and operating systems.
- User authentication and authorization mechanisms for secure access control.
- Session management and monitoring capabilities for enhanced security and control.
- Customization options to tailor the solution to specific business requirements.
Pricing models for commercial SSH over WebSockets solutions vary depending on the provider and the features offered. Some solutions offer subscription-based pricing, while others may charge a one-time fee or a combination of both. It’s important to evaluate the pricing structure and choose the option that best aligns with your budget and usage requirements.
Support Options
Commercial SSH over WebSockets solutions typically provide support services to assist customers with installation, configuration, troubleshooting, and ongoing maintenance. These support options may include:
- Documentation and tutorials for self-guided setup and troubleshooting.
- Technical support via email, phone, or online chat for prompt assistance.
- Regular updates and security patches to ensure the solution remains secure and up-to-date.
- Customization and integration services to tailor the solution to specific business needs.
Table of Key Features and Benefits
The following table provides a comparison of the key features and benefits of different commercial SSH over WebSockets solutions:
| Feature | Solution A | Solution B | Solution C |
|---|---|---|---|
| Cross-platform Compatibility | Windows, macOS, Linux | Windows, macOS, Linux, Android, iOS | Windows, macOS, Linux, Android, iOS, Chrome OS |
| User Authentication and Authorization | Password, SSH keys, Two-Factor Authentication (2FA) | Password, SSH keys, 2FA, Certificate-Based Authentication | Password, SSH keys, 2FA, Certificate-Based Authentication, Single Sign-On (SSO) |
| Session Management and Monitoring | Session logging, Real-time monitoring, Session recording | Session logging, Real-time monitoring, Session recording, Session hijacking protection | Session logging, Real-time monitoring, Session recording, Session hijacking protection, Idle session timeout |
| Customization Options | Custom branding, White-labeling, Plugin support | Custom branding, White-labeling, Plugin support, Custom scripting | Custom branding, White-labeling, Plugin support, Custom scripting, API integration |
| Pricing Model | Subscription-based (monthly or annual) | One-time fee or Subscription-based (monthly or annual) | One-time fee or Subscription-based (monthly or annual) with additional charges for premium features |
| Support Options | Documentation, Email support, Phone support | Documentation, Email support, Phone support, Live chat support | Documentation, Email support, Phone support, Live chat support, Customization and integration services |
Future Trends and Developments
The realm of SSH over WebSockets is poised for significant advancements and innovative applications. Emerging trends and developments are shaping the future of this technology, offering potential benefits and challenges.
One notable trend is the integration of SSH over WebSockets with emerging technologies such as artificial intelligence (AI) and machine learning (ML). This convergence can enhance the security and efficiency of remote access and secure communication. AI and ML algorithms can analyze network traffic patterns, identify anomalies, and detect potential threats in real-time, providing proactive protection against cyberattacks.
Potential Challenges and Opportunities
Despite its advantages, SSH over WebSockets also faces certain challenges. One challenge lies in ensuring interoperability and compatibility across different platforms and devices. Standardization efforts are underway to address this issue, promoting the development of common protocols and standards that facilitate seamless integration and communication between various systems.
Another challenge is maintaining a balance between security and usability. While SSH over WebSockets offers robust security features, it is crucial to ensure that these features do not hinder the user experience. Finding the right balance between security and usability is essential for widespread adoption.
Speculations on the Future
Looking ahead, the future of SSH over WebSockets appears promising. With the continuous evolution of technology and the growing demand for secure remote access, SSH over WebSockets is likely to become an integral part of modern communication infrastructure.
As technology advances, SSH over WebSockets may find applications in new and unforeseen areas. The integration of SSH over WebSockets with emerging technologies such as the Internet of Things (IoT) and edge computing holds immense potential for secure communication and remote management of devices.
Conclusion SSH over WebSockets

In this comprehensive exploration of SSH over WebSockets, we’ve delved into the intricacies of this powerful technology, unveiling its benefits, applications, and potential impact on various industries. SSH over WebSockets has emerged as a game-changer in secure remote access, offering a seamless and versatile solution for managing and controlling remote systems and devices.
By leveraging the ubiquitous nature of WebSockets, SSH over WebSockets has opened up new possibilities for remote connectivity, enabling real-time communication, interactive terminal sessions, and secure file transfers across different platforms and devices. Its ability to seamlessly integrate with existing web applications and services makes it an ideal choice for modern web-based applications that require secure remote access capabilities.
Benefits and Applications
The benefits of SSH over WebSockets are numerous and far-reaching. Its platform-independent nature allows for seamless connectivity across various operating systems and devices, enhancing accessibility and flexibility. The real-time communication capabilities enable interactive terminal sessions, providing a responsive and immersive user experience.
Additionally, the secure file transfer feature ensures the integrity and confidentiality of sensitive data during transmission.
SSH over WebSockets finds applications in diverse industries, including IT management, DevOps, system administration, remote desktop access, and industrial automation. It empowers IT professionals, system administrators, and developers to securely access and manage remote systems, perform remote diagnostics, and troubleshoot issues in real-time.
Moreover, it enables remote workers and distributed teams to securely connect to their work environments from anywhere, fostering collaboration and productivity.
Call to Action
With its compelling advantages and wide-ranging applications, SSH over WebSockets presents a compelling opportunity for businesses and organizations to enhance their remote connectivity and security. We encourage readers to explore the possibilities of SSH over WebSockets and consider implementing it in their projects.
Embrace the transformative power of this technology and unlock the full potential of secure remote access and management.
Summary
SSH over WebSockets has revolutionized the way we access and manage remote systems, providing a secure, real-time, and efficient communication channel. Its versatility and wide range of applications make it an invaluable tool for system administrators, DevOps engineers, and anyone requiring secure remote access.
As technology continues to advance, SSH over WebSockets will undoubtedly play an increasingly significant role in shaping the future of remote connectivity and secure communication.