Welcome to the world of secure and remote access with Termux SSH Server! This comprehensive guide will empower you to establish a robust SSH server on your Termux environment, enabling you to manage your devices and access your data from anywhere in the world.
Whether you’re a seasoned IT professional or a curious tech enthusiast, this guide will equip you with the knowledge and skills to harness the full potential of Termux SSH Server.
In this guide, we’ll delve into the intricacies of Termux SSH Server, covering everything from its setup and configuration to advanced features and troubleshooting. We’ll also provide practical examples and best practices to ensure your SSH server is secure, reliable, and tailored to your specific needs.
So, buckle up and let’s embark on this exciting journey into the world of remote connectivity and secure data management.
Termux SSH Server Setup
Setting up an SSH server on Termux is a straightforward process that enables secure remote access to your Android device. By following these steps, you can establish an SSH server on Termux and configure it for secure connections.
Generating SSH Keys
To generate SSH keys, execute the following commands:
- `ssh-keygen
- t rsa
- b 4096`
- Enter a secure passphrase for your SSH key.
- The generated keys will be stored in ~/.ssh/id_rsa (private key) and ~/.ssh/id_rsa.pub (public key).
Configuring the SSH Server
To configure the SSH server, follow these steps:
Install the SSH server package
`pkg install openssh`
Start the SSH server
`sshd`
Allow SSH connections through the firewall
`termux-setup-storage`
Open port 22 in the firewall
`ufw allow 22`
Configure the SSH server in `/etc/ssh/sshd_config`
Set `PasswordAuthentication` to `no`
Set `PermitRootLogin` to `no`
Set `AuthorizedKeysFile` to `~/.ssh/authorized_keys`
Restart the SSH server
`service sshd restart`
Securing Termux SSH Server
Securing your Termux SSH server is paramount to protect it from unauthorized access and potential cyber threats. Employing best practices, such as password authentication, key-based authentication, and firewall configuration, is crucial to safeguard your server and ensure its integrity.
Password Authentication
Password authentication is a simple method of authenticating users, but it’s less secure than key-based authentication. If using password authentication, choose strong, complex passwords and enable two-factor authentication for added protection.
Key-Based Authentication
Key-based authentication is a more secure alternative to password authentication. It involves using public-private key pairs to establish a secure connection. Generate a public-private key pair and add the public key to the authorized_keys file on your server.
Firewall Configuration
Configure a firewall to restrict access to your SSH server and prevent unauthorized connections. Enable only the necessary ports and IP addresses, and consider using a firewall tool like UFW to set up rules and monitor traffic.
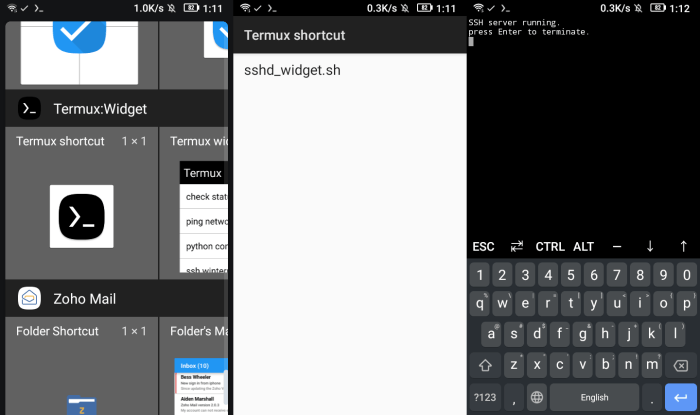
Connecting to Termux SSH Server
Establishing a connection to your Termux SSH server allows you to access your device remotely and securely. To connect, you’ll need an SSH client. Various clients are available for different operating systems.
Connecting from Windows
Windows users can utilize the built-in PowerShell or command prompt. Enter the following command, replacing with your Termux username and with the IP address of your device:
ssh @
Connecting from macOS
On macOS, use the Terminal application. Run the following command, replacing and accordingly:
ssh @
Connecting from Linux
For Linux users, open a terminal and execute the command:
ssh @
Port Forwarding with Termux SSH Server
Port forwarding is a technique that allows you to access a service running on a remote machine through an SSH tunnel. This is useful for securely accessing services that are not accessible directly from the internet, such as a local web server or database.
With Termux, you can easily set up SSH tunnels using the -L option. The following command creates an SSH tunnel that forwards local port 8080 to remote port 80 on the server:
“` ssh -L 8080:localhost:80 user@server “`
Once the tunnel is established, you can access the remote web server by visiting http://localhost:8080 in your browser.
You can also forward specific ports using the -R option. The following command forwards remote port 22 on the server to local port 8022:
“` ssh -R 8022:localhost:22 user@server “`
This allows you to access the SSH server on the remote machine by connecting to localhost:8022 on your local machine.
Port forwarding is a powerful tool that can be used to securely access remote services and applications. It is a valuable feature of the Termux SSH server that can be used for a variety of purposes.
Using Termux SSH Server for Remote Access
The Termux SSH server can be utilized for remote access to a device, enabling users to manage files, execute commands, and control applications remotely.
Accessing Files
Using SSH, users can access files on the remote device as if they were on their local system. File transfer protocols like SCP or SFTP can be employed for secure file transfers.
Running Commands
The SSH terminal allows users to execute commands on the remote device, granting them the ability to install software, update the system, or perform other administrative tasks remotely.
Managing Applications
With SSH, users can remotely manage applications on the device, including starting, stopping, or updating them. This capability simplifies application management and allows for remote troubleshooting.
Customizing Termux SSH Server
The Termux SSH server offers a range of customization options to tailor it to your specific needs. By modifying the configuration, you can enhance security, improve usability, and optimize performance.
Changing SSH Port
To change the default SSH port, edit the /data/data/com.termux/files/usr/etc/sshd_config file and locate the Port directive. Replace the default port (usually 8022) with your desired port number.
Setting Up Banner Message
You can display a custom banner message to users when they connect to your SSH server. To do this, add the following line to the sshd_config file:
Banner /path/to/banner.txt
Replace /path/to/banner.txt with the path to a text file containing your banner message.
Configuring Session Settings
The sshd_config file also allows you to configure various session settings. For example, you can:
- Set the maximum number of concurrent connections with the
MaxSessionsdirective. - Restrict access to specific users or groups using the
AllowUsersandAllowGroupsdirectives. - Configure password authentication with the
PasswordAuthenticationdirective. - Enable key-based authentication with the
AuthorizedKeysFiledirective.
Troubleshooting Termux SSH Server
The Termux SSH server, while robust, may encounter issues. Identifying and resolving these issues is crucial for maintaining a secure and reliable connection.
Common problems include:
Connection Refused
This error indicates that the SSH server is not running or is not listening on the specified port. Verify that the server is active and that the port is correct.
Permission Denied
This error occurs when the user attempting to connect does not have the necessary permissions to access the SSH server. Ensure that the user has been granted appropriate access rights.
Authentication Failed
This error indicates that the provided credentials are incorrect. Verify the username and password or use an alternative authentication method, such as SSH keys.
Network Issues
Network problems, such as firewalls or connectivity issues, can disrupt SSH connections. Check network settings and ensure that the SSH server is accessible from the client.
Configuration Errors
Incorrect SSH server configuration can lead to various issues. Review the SSH configuration file (/etc/ssh/sshd_config) and ensure that it is set up correctly.
Advanced Features of Termux SSH Server
The Termux SSH server offers advanced features that enhance its functionality and security. These include:
SSH Agent Forwarding
Allows users to seamlessly access SSH keys stored on their local machine, eliminating the need to manually transfer keys.
Public Key Authentication
Enables users to authenticate to the server using a public key instead of a password, providing an extra layer of security.
User Permissions Management
Grants administrators the ability to create and manage user accounts, assign permissions, and restrict access to specific directories or commands.
Comparison of Termux SSH Server with Other SSH Servers
Termux SSH server is a versatile and feature-rich SSH server for Android devices. However, it is essential to compare its capabilities with other popular SSH servers to understand its strengths and limitations.
One key aspect to consider is the range of supported protocols and ciphers. Termux SSH server supports SSH protocols 1 and 2, as well as a variety of encryption algorithms, including AES, 3DES, and Blowfish. This provides a good level of security and compatibility with various clients.
OpenSSH
OpenSSH is a widely used and well-established SSH server. It offers a comprehensive set of features, including support for multiple protocols (SSH 1 and 2), a wide range of ciphers, and advanced authentication methods (e.g., public key authentication, two-factor authentication).
OpenSSH is also highly customizable and extensible through plugins.
Advantages: Extensive feature set, strong security, customizable, widely supported
Disadvantages: Can be complex to configure, may not be suitable for resource-constrained devices
Dropbear
Dropbear is a lightweight and portable SSH server designed for embedded systems and devices with limited resources. It supports SSH protocol 2, a subset of ciphers, and basic authentication methods. Dropbear is known for its small footprint and low memory consumption, making it suitable for devices with limited hardware capabilities.
Advantages: Lightweight, low resource consumption, easy to configure
Disadvantages: Limited feature set, fewer supported protocols and ciphers
Comparison Summary
The table below summarizes the key differences between Termux SSH server, OpenSSH, and Dropbear:
| Feature | Termux SSH Server | OpenSSH | Dropbear |
|---|---|---|---|
| Supported Protocols | SSH 1, SSH 2 | SSH 1, SSH 2 | SSH 2 |
| Encryption Algorithms | AES, 3DES, Blowfish | AES, 3DES, Blowfish, ChaCha20 | AES, 3DES |
| Authentication Methods | Password, public key | Password, public key, two-factor authentication | Password, public key |
| Customization | Limited | Highly customizable | Limited |
| Resource Consumption | Moderate | High | Low |
Ultimately, the choice of SSH server depends on the specific requirements and constraints of the intended use case. Termux SSH server offers a good balance of features and resource consumption, making it suitable for a wide range of Android devices.
OpenSSH provides a more comprehensive feature set and advanced security options, but it may not be suitable for resource-constrained devices. Dropbear is a lightweight and efficient option for devices with limited hardware capabilities.
Creating a Secure and Reliable SSH Server with Termux
Establishing a secure and reliable SSH server with Termux involves meticulous planning and configuration. This guide provides a comprehensive roadmap to ensure your server’s integrity and reliability.
Choosing the Right SSH Configuration
Configure SSH settings to optimize security and functionality. Enable strong encryption algorithms, such as AES-256-CBC, and disable weak ciphers. Use public-key authentication instead of passwords to prevent unauthorized access. Limit the number of concurrent SSH sessions and set up a fail2ban system to block repeated login attempts.
Setting Up a Firewall
Implement a firewall to restrict unauthorized access to your server. Allow only necessary ports, such as SSH (port 22), and block all other incoming traffic. Use iptables or a similar firewall tool to define rules and protect your server from malicious attacks.
Monitoring the Server
Regularly monitor your SSH server to detect suspicious activity and ensure its stability. Use tools like fail2ban to track failed login attempts and block potential attackers. Implement log monitoring to analyze server activity and identify any irregularities. Consider using intrusion detection systems (IDS) to detect and respond to malicious behavior.
Final Summary

Congratulations! You’ve now mastered the art of setting up and securing a Termux SSH Server. With the knowledge and skills you’ve gained from this guide, you can confidently manage your devices, access your data remotely, and enjoy the benefits of secure and reliable SSH connectivity.
Remember, the world of technology is constantly evolving, so stay curious, keep learning, and explore the endless possibilities that Termux SSH Server has to offer.