Secure Shell (SSH) is an essential tool for remote server management, providing a secure and encrypted channel for accessing and controlling systems over a network. In this guide, we will delve into the intricacies of installing and configuring an SSH server on Linux Mint, empowering you to harness the full potential of this powerful protocol.
SSH offers a plethora of benefits, including secure remote access, file transfer, and command execution. By understanding the installation and configuration process, you can unlock these capabilities and enhance the security and efficiency of your Linux Mint system.
Installation Procedures
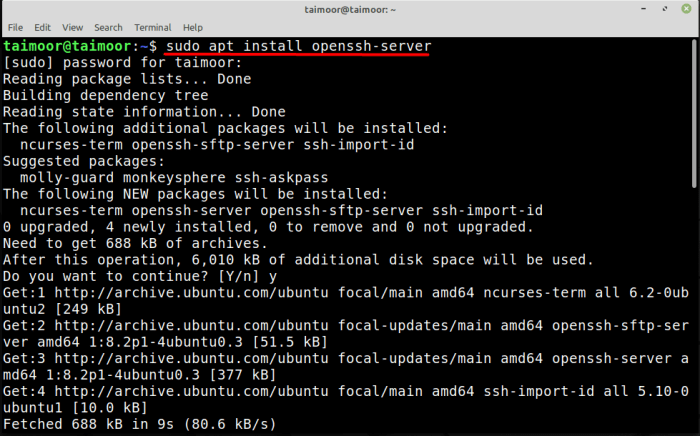
To install an SSH server on Linux Mint, you need to install the OpenSSH server package.
You can do this by opening a terminal and typing the following command:
sudo apt install openssh-server
Once the package is installed, you need to start the SSH server.
You can do this by typing the following command:
sudo systemctl start ssh
You can now connect to your SSH server using a client such as PuTTY or OpenSSH.
Configuring the SSH Server
You can configure the SSH server by editing the configuration file located at /etc/ssh/sshd_config .
Some common configuration options include:
- Port: The port that the SSH server listens on. The default port is 22.
- Protocol: The SSH protocol version that the server supports. The default is 2.
- Ciphers: The encryption algorithms that the server supports. The default is a list of strong ciphers.
- MACs: The message authentication codes that the server supports. The default is a list of strong MACs.
- Key Exchange Algorithms: The key exchange algorithms that the server supports. The default is a list of strong key exchange algorithms.
- Host Keys: The host keys that the server uses to authenticate itself to clients. The default is to generate a new host key on first startup.
You can also configure the SSH server to use public key authentication.
This is a more secure way to authenticate users because it does not require them to enter a password.
To configure public key authentication, you need to generate a public key and a private key.
You can do this by typing the following command:
ssh-keygen -t rsa
Once you have generated a public key and a private key, you need to add the public key to the ~/.ssh/authorized_keys file on the server.
You can do this by typing the following command:
cat ~/.ssh/id_rsa.pub >> ~/.ssh/authorized_keys
You can now connect to your SSH server using public key authentication.
Configuration Options
The SSH server offers a range of configuration options that allow you to customize its behavior and security settings. Understanding and adjusting these parameters is crucial for maintaining a secure and efficient SSH environment.
Key parameters include:
- Port: Specifies the TCP port on which the SSH server listens for incoming connections. The default port is 22, but you can change it for security reasons.
- Protocol: Defines the SSH protocol version to be used. SSHv2 is the recommended version due to its enhanced security features.
- Ciphers: Specifies the encryption algorithms used to protect data transmitted over the SSH connection. Stronger ciphers provide better security but may impact performance.
- MACs: Defines the message authentication codes used to ensure data integrity. Stronger MACs provide better protection against data tampering.
- Key Exchange Algorithms: Determines the algorithms used to establish a secure session key between the client and server.
- Host Keys: Public-private key pairs used to authenticate the SSH server to clients. Multiple host keys can be configured for different purposes.
By carefully configuring these parameters, you can tailor the SSH server to meet your specific security and performance requirements.
Common Configurations
Here are some common configuration examples:
- Restricting Access: To limit SSH access to specific users or groups, use the
AllowUsersandAllowGroupsdirectives in the SSH configuration file. - Disabling Password Authentication: To enhance security, you can disable password authentication by setting
PasswordAuthenticationtonoin the SSH configuration file. - Using SSH Keys: For secure authentication, generate SSH key pairs and configure the server to use them by specifying the
AuthorizedKeysFiledirective in the SSH configuration file.
Security Considerations
SSH is a powerful tool, but it also poses potential security risks. It’s crucial to be aware of these risks and take appropriate measures to mitigate them.
One of the main security concerns with SSH is unauthorized access. Attackers may attempt to gain access to your server by exploiting vulnerabilities in the SSH server software or by brute-forcing passwords. To prevent unauthorized access, it’s essential to keep the SSH server software up-to-date and use strong passwords.
Hardening SSH Configurations
There are several best practices you can follow to harden your SSH configurations and improve security:
- Disable root login: Restrict direct login as the root user and create a separate user account with administrative privileges.
- Use key-based authentication: SSH key-based authentication is more secure than password-based authentication. Generate SSH keys and configure your server to accept only key-based authentication.
- Limit access to trusted IP addresses: Configure your SSH server to only allow connections from specific IP addresses or subnets. This can help prevent unauthorized access attempts from untrusted sources.
- Enable SSH port knocking: SSH port knocking is a technique that involves sending a specific sequence of packets to a closed SSH port. Once the correct sequence is received, the SSH port is opened for a short period of time. This makes it more difficult for attackers to brute-force their way into your server.
- Monitor SSH logs: Regularly review your SSH logs for any suspicious activity. This can help you detect unauthorized access attempts or other security incidents.
Client Connection
Connecting to an SSH server involves establishing a secure connection between a client machine and the server. This process requires the use of SSH software on the client machine.
SSH Connection Methods
There are several methods to connect to an SSH server:
-
- -*Terminal-based
Using a terminal emulator or command prompt to establish the connection.
- -*Terminal-based
-*Graphical user interface (GUI)
Using SSH clients with graphical interfaces, such as PuTTY or Cyberduck.
-*Integrated development environments (IDEs)
Some IDEs, like Visual Studio Code, have built-in SSH functionality.
SSH Connection Options
When connecting to an SSH server, various options can be specified to customize the connection:
-
- -*-p
Specifies the port number for the SSH connection (default is 22).
- -*-p
-*-i
Specifies the path to a private key file for authentication.
-*-u
Specifies the username for authentication.
-*-h
Displays help information.
Using SSH Commands
To connect to an SSH server using the terminal, the following command is used:“`ssh [options] user@host“`Replace [options] with the desired options (e.g.,
- p,
- i) and user@host with the username and hostname of the server.
Remote Management
SSH enables secure remote management of your server from any location with an internet connection. It provides a command-line interface that allows you to execute commands, transfer files, and manage the system remotely.
Common SSH Commands and Operations
- ssh user@server_ip: Establish an SSH connection to the server.
- ls: List files and directories.
- cd directory: Change the current working directory.
- sudo command: Execute a command with root privileges.
- scp file user@server_ip:destination: Securely copy a file to the remote server.
- scp user@server_ip:file destination: Securely copy a file from the remote server.
Best Practices for Remote Access
To ensure secure and efficient remote management, follow these best practices:
- Use strong passwords or SSH keys: Protect your SSH access with complex passwords or SSH keys.
- Limit root access: Avoid using the root account for daily tasks. Create a dedicated user with sudo privileges instead.
- Enable SSH key-based authentication: This provides a more secure alternative to password-based authentication.
- Disable password authentication: Consider disabling password authentication altogether for added security.
- Use a firewall: Configure a firewall to restrict SSH access to trusted IP addresses or subnets.
Advanced Features
SSH offers advanced features beyond secure remote access, such as port forwarding and tunneling. These capabilities extend SSH’s functionality and provide additional benefits for various use cases.
Port Forwarding
Port forwarding allows you to redirect traffic from one port on your local machine to a different port on a remote server. This technique is particularly useful for accessing services that are not directly accessible from the Internet. For example, you can set up port forwarding to access a local web server from a remote location.Configuration:“`ssh
-L
: @ “`
Tunneling
Tunneling creates a secure, encrypted channel between two remote hosts over an SSH connection. This allows you to establish secure connections between systems that may not be directly accessible or may have firewall restrictions. Tunneling can be used for various applications, such as remote desktop access, file transfer, and network management.Configuration:“`ssh
-L
: @ ssh
-R
: @ “`These advanced features enhance the versatility of SSH, enabling you to establish secure connections, redirect traffic, and access remote resources in a flexible and secure manner.
Troubleshooting
During the installation or usage of SSH, certain common problems may arise. Here are some troubleshooting tips and solutions:
Error: Permission denied (publickey)
This error occurs when the user’s public key is not authorized on the server. To fix it, add the user’s public key to the authorized_keys file on the server.
Error: Connection refused
This error indicates that the SSH server is not running or listening on the specified port. Ensure that the SSH server is running and that the firewall is not blocking the connection.
Error: Host key verification failed
This error occurs when the host key of the server does not match the one stored in the known_hosts file. To fix it, remove the existing host key from the known_hosts file and reconnect to the server.
SSH with Other SSH Implementations
SSH can be used with various SSH implementations, such as OpenSSH. Here are the key differences and similarities between SSH and OpenSSH:
Key Differences
- Package Management: SSH is typically included in the base operating system, while OpenSSH is distributed as a separate package.
- Configuration Files: SSH uses /etc/ssh/sshd_config for server configuration and ~/.ssh/config for client configuration. OpenSSH uses /etc/ssh/sshd_config and ~/.ssh/config for both server and client configurations.
- Command-Line Interface (CLI): SSH uses the ssh command for client operations and sshd for server operations. OpenSSH uses the same commands, but with slightly different options and syntax.
- Features: OpenSSH offers additional features such as SSH agent forwarding, port knocking, and improved support for SSH keys.
Key Similarities
- Core Functionality: Both SSH and OpenSSH provide secure remote access, file transfer, and port forwarding.
- Encryption and Authentication: Both implementations use strong encryption algorithms and support various authentication methods, including passwords, SSH keys, and two-factor authentication.
- Cross-Platform Support: SSH and OpenSSH are available for a wide range of operating systems, including Linux, macOS, Windows, and mobile devices.
Comparison Table
| Feature | SSH | OpenSSH ||—|—|—|| Package Management | Included in base OS | Separate package || Configuration Files | /etc/ssh/sshd_config, ~/.ssh/config (client only) | /etc/ssh/sshd_config, ~/.ssh/config (both) || Command-Line Interface | ssh, sshd | ssh, sshd (with slightly different options) || Features | Basic SSH functionality | Additional features (e.g.,
agent forwarding, port knocking) |
SSH in Linux Mint Use Cases
SSH offers numerous practical use cases in Linux Mint, significantly enhancing productivity and efficiency.
SSH enables secure remote access to your Linux Mint system, allowing you to manage and control it from anywhere with an internet connection. This capability proves invaluable for system administrators, remote workers, and users who need to access their computers remotely.
Remote System Management
SSH empowers you to perform administrative tasks on remote Linux Mint systems, eliminating the need for physical access. You can execute commands, install software, update the system, and troubleshoot issues remotely. This functionality is particularly useful for managing multiple servers or systems located in different physical locations.
Secure File Transfer
SSH provides a secure channel for transferring files between remote systems. Using the “scp” command, you can securely copy files between your local and remote Linux Mint systems, ensuring data integrity and confidentiality during transmission.
Port Forwarding
SSH allows you to forward ports between your local and remote systems, creating secure tunnels for accessing services that may be blocked or inaccessible from your local network. This capability enables you to access remote databases, web servers, or other applications that require specific ports.
Remote Desktop Access
By combining SSH with X forwarding, you can establish a secure graphical connection to your remote Linux Mint system. This allows you to access and control the remote desktop as if you were physically present, enabling you to run graphical applications and interact with the system’s graphical user interface (GUI).
Best Practices for SSH Usage
To ensure secure and efficient SSH usage, adhering to best practices is crucial. These guidelines encompass password management, key authentication, session management, and more.
By following these best practices, you can minimize security risks and enhance the effectiveness of your SSH operations.
Password Management
- Use strong, complex passwords that are difficult to guess.
- Avoid using common passwords or personal information.
- Change your password regularly, at least every 90 days.
- Use a password manager to securely store and manage your passwords.
Key Authentication
Key authentication is a more secure alternative to password authentication. It involves using public and private key pairs to establish a secure connection.
- Generate a strong public-private key pair using a reputable SSH key generator.
- Keep your private key secure and never share it with anyone.
- Configure your SSH server to accept key authentication and restrict password authentication.
Session Management
- Use SSH with caution, especially on public networks.
- Disable SSH access when not in use.
- Monitor SSH logs regularly for any suspicious activity.
- Use SSH tunneling to securely access other services over an insecure network.
Outcome Summary
Mastering SSH on Linux Mint empowers you with a robust and versatile tool for remote system management. Whether you’re a seasoned Linux user or just starting your journey, this guide has equipped you with the knowledge and skills to leverage SSH effectively.
Embrace the power of secure remote access, harness the efficiency of command execution, and elevate your Linux Mint experience to new heights.